As enterprise networks evolve, traditional campus architectures often struggle with increasing demands for automation, security, and scalability. Cisco Software-Defined Access (SD-Access) emerges as the answer—a network fabric that reimagines how campus networks are designed, deployed, and managed.
This blog dives into the core concepts of SD-Access, focusing on its architecture, control and data planes, fabric overlays, and the coexistence strategy with traditional networks.
Why SD-Access Is a Paradigm Shift
Conventional campus designs rely heavily on manual configuration, VLAN sprawl, and inefficient access control methods. SD-Access simplifies these by abstracting the underlying network and introducing centralized policy, segmentation, and automation—all powered by Cisco DNA Center.
Key Concepts
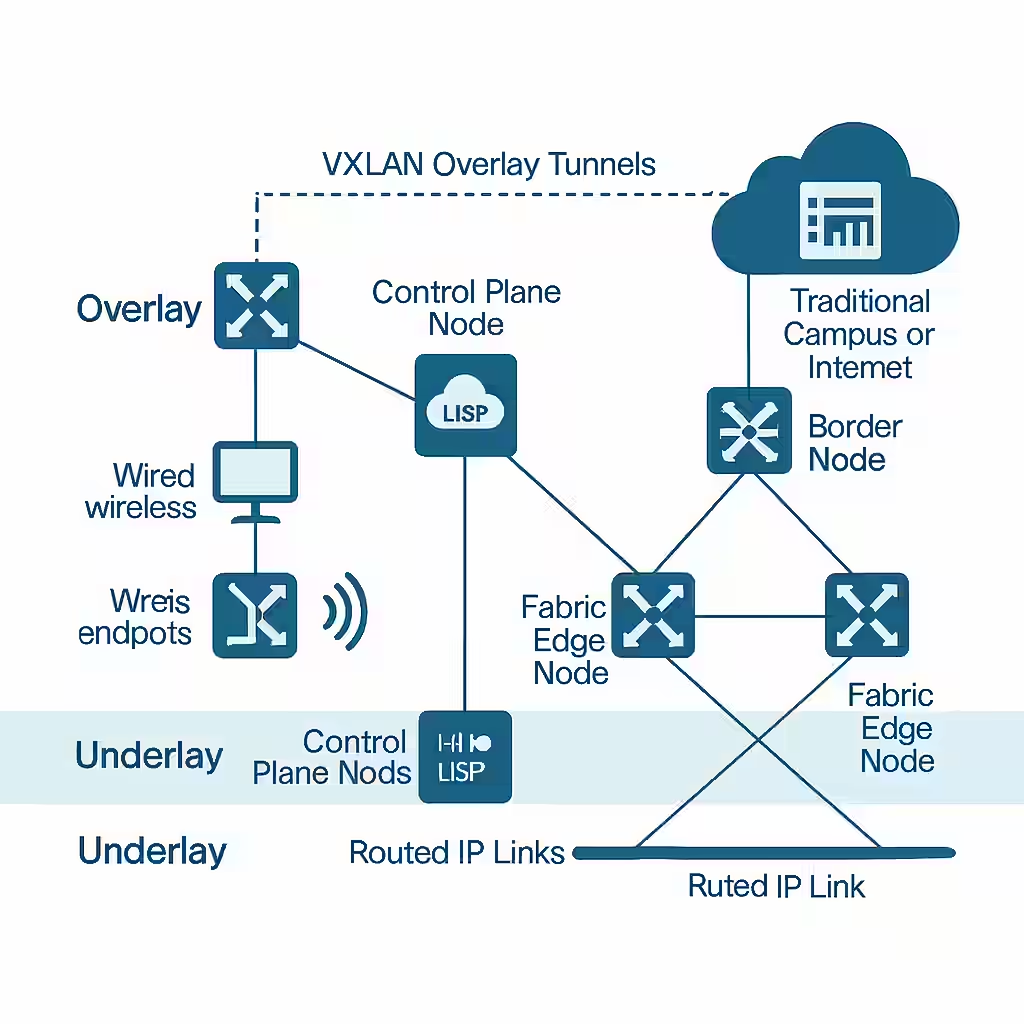
SD-Access Architecture Overview
At its core, SD-Access is a fabric-based network model where endpoints are decoupled from their physical locations. It introduces new roles and concepts:
- Underlay: The foundational IP transport network (typically Layer 3), connecting all fabric nodes.
- Overlay: The logical network built on top of the underlay, using tunneling (VXLAN) for segmentation and traffic forwarding.
- Control Plane: A distributed database (LISP-based) that maps user/device identity to their current location.
- Data Plane: VXLAN tunnels that forward encapsulated traffic across the fabric.
Components of the SD-Access Fabric
- Fabric Edge Nodes: Access-layer switches where endpoints connect; they encapsulate traffic into VXLAN.
- Fabric Control Plane Node: Maintains endpoint location information using LISP; enables identity-based routing.
- Fabric Border Node: Acts as the gateway between the SD-Access fabric and external networks (e.g., internet, non-fabric).
- Fabric Wireless Controller: Integrates wireless traffic into the fabric using CAPWAP tunnels from access points.
- DNA Center (DNAC): The central controller for policy, provisioning, and assurance in SD-Access.
Control and Data Plane Deep Dive
Control Plane (LISP – Locator/ID Separation Protocol)
- Maintains a mapping database of Endpoint ID (EID) to Routing Locator (RLOC).
- Enables seamless mobility—users can roam the network while retaining their IP and policy.
Data Plane (VXLAN Tunneling)
- Provides Layer 2 and Layer 3 segmentation via encapsulated traffic.
- Supports scalable group segmentation (SGT) for enforcing policies between different user or device groups.
Overlay Fabric Communication
- When an endpoint connects, the fabric edge node queries the control plane for the destination location.
- Once located, a VXLAN tunnel is built dynamically to the corresponding fabric node for traffic forwarding.
Traditional Campus Network Integration
SD-Access does not demand a rip-and-replace strategy. It can coexist with traditional campus networks:
- Via Border Nodes: The SD-Access fabric connects to legacy Layer 2/Layer 3 domains through the border node, preserving interoperability.
- Shared Services: DNS, DHCP, or internet access can reside outside the fabric but be accessible through policies.
- Staging Migration: Organizations can transition floor-by-floor or building-by-building to SD-Access.
Considerations for Design and Deployment
- Underlay Design: Ensure reliable IP connectivity—often using IS-IS or OSPF.
- Control Plane Redundancy: Deploy multiple control nodes for high availability.
- Segmentation Strategy: Plan VRFs and SGTs early to align with business groups.
- Wireless Integration: Use Fabric Mode WLCs and APs to fully extend the fabric to wireless clients.
- Monitoring: Leverage DNA Center Assurance for deep insights and anomaly detection.
Config Insight: Verifying VXLAN Tunnel on Edge Node
show fabric vn-segment
This command provides information about VXLAN tunnels and segment IDs on Cisco fabric-enabled switches.