Sometimes, defeat comes even when someone gives their best—and it hurts. But defeat has a way of teaching humility. It reminds us that not every closed door is a failure, but a redirection. The job that didn’t choose them isn’t the end of the road. It’s a step toward something better, something more aligned. Stay humble, stay ready, and keep moving forward. #StayHopeful
Author: Sun
-
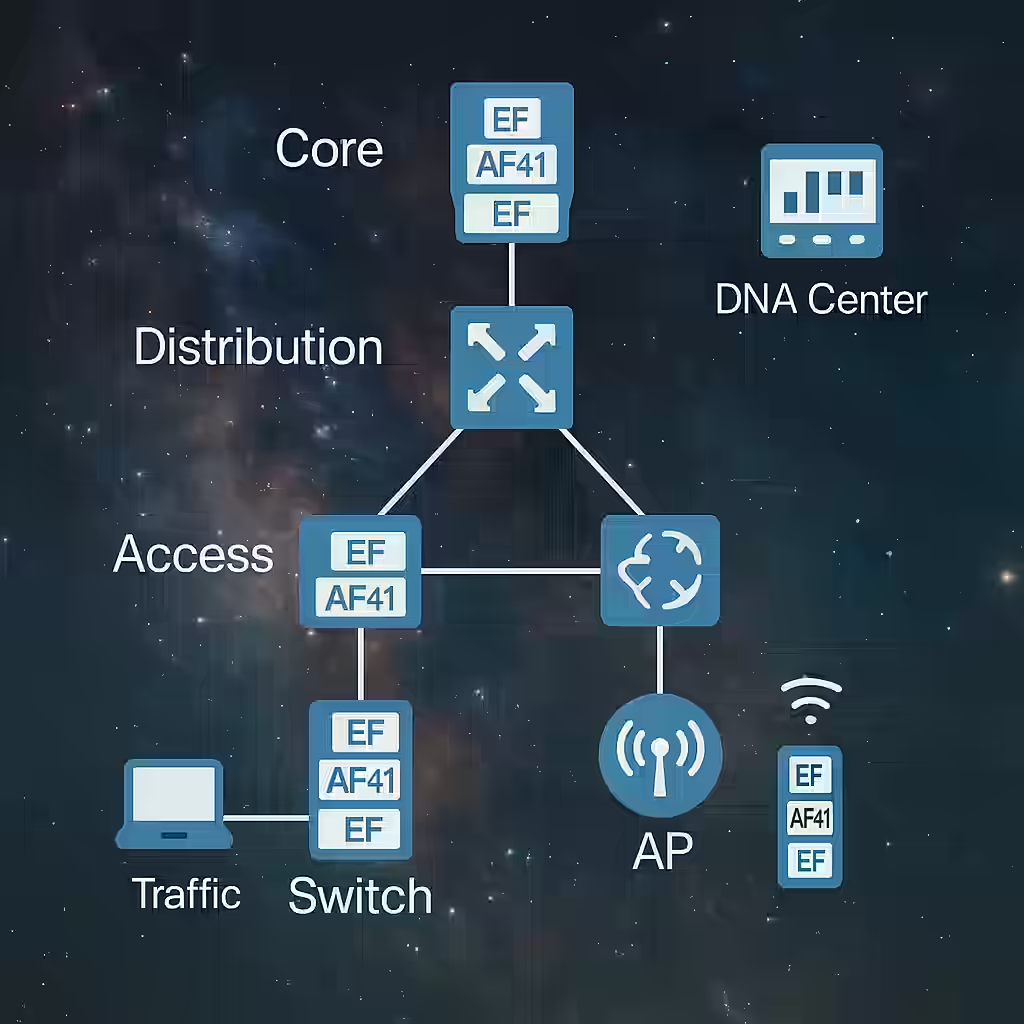
Taming the Traffic Jungle: Wired and Wireless QoS Concepts for Enterprise Networks
Enterprise networks handle a wild mix of traffic—video calls, file transfers, cloud apps, and more—all competing for the same resources. Quality of Service (QoS) is the mechanism that brings order to this chaos, ensuring that critical applications get the performance they need.
This blog breaks down the core concepts of QoS across both wired and wireless networks, explaining queuing, marking, policing, and shaping, and how policies drive traffic prioritization.
Why QoS Matters in Enterprise Networks
Without QoS, all traffic is treated equally—first come, first served. In peak hours, time-sensitive traffic like voice and video suffers, resulting in jitter, delay, or drops. QoS ensures that high-priority applications consistently perform well, even under congestion.
Key Concepts
1. Classification and Marking
Classification identifies traffic types (e.g., voice, video, web), while marking tags packets so network devices can treat them accordingly.
- Wired Networks: Use Layer 2 CoS (Class of Service) or Layer 3 DSCP (Differentiated Services Code Point) markings.
- Wireless Networks: Mapping occurs between DSCP and wireless QoS profiles (WMM Access Categories).
Example:
- DSCP EF (Expedited Forwarding, value 46) is often used for voice.
- DSCP AF41 is suitable for video conferencing.
2. Queuing
When traffic exceeds interface capacity, packets are placed in queues. Queuing mechanisms determine which packets are sent first.
- FIFO (First-In, First-Out): No prioritization.
- CBWFQ (Class-Based Weighted Fair Queuing): Allocates bandwidth per traffic class.
- LLQ (Low Latency Queuing): Adds a strict-priority queue for delay-sensitive traffic like VoIP.
3. Policing and Shaping
Policing drops or re-marks excess traffic instantly; shaping buffers and sends it at a regulated rate.
- Policing: Common on inbound traffic, ensuring users/applications don’t exceed allowed rates.
- Shaping: Used outbound to smooth bursty traffic, often paired with queuing.
4. Trust Boundaries
Define where markings are accepted or rewritten. For example, in a wireless deployment, trust is usually given to the AP if it’s known to enforce QoS settings accurately.
QoS in Wireless Networks
Wireless adds extra complexity due to shared medium and variable transmission conditions.
- WMM (Wi-Fi Multimedia) defines 4 Access Categories:
- Voice (AC_VO)
- Video (AC_VI)
- Best Effort (AC_BE)
- Background (AC_BK)
APs translate DSCP into WMM categories, ensuring consistent QoS treatment end-to-end.
Important: Congestion can occur on both the wired uplink and the wireless RF. QoS must be applied at both points.
Policy-Driven QoS
QoS policies use class maps, policy maps, and service policies in Cisco IOS.
- Class Map: Matches traffic types.
- Policy Map: Assigns QoS actions like bandwidth or marking.
- Service Policy: Applies the policy to an interface.
Config Insight: Simple LLQ for Voice Traffic
class-map match-any VOICE match ip dscp ef policy-map QOS_POLICY class VOICE priority 1000 class class-default fair-queue interface GigabitEthernet0/1 service-policy output QOS_POLICY -
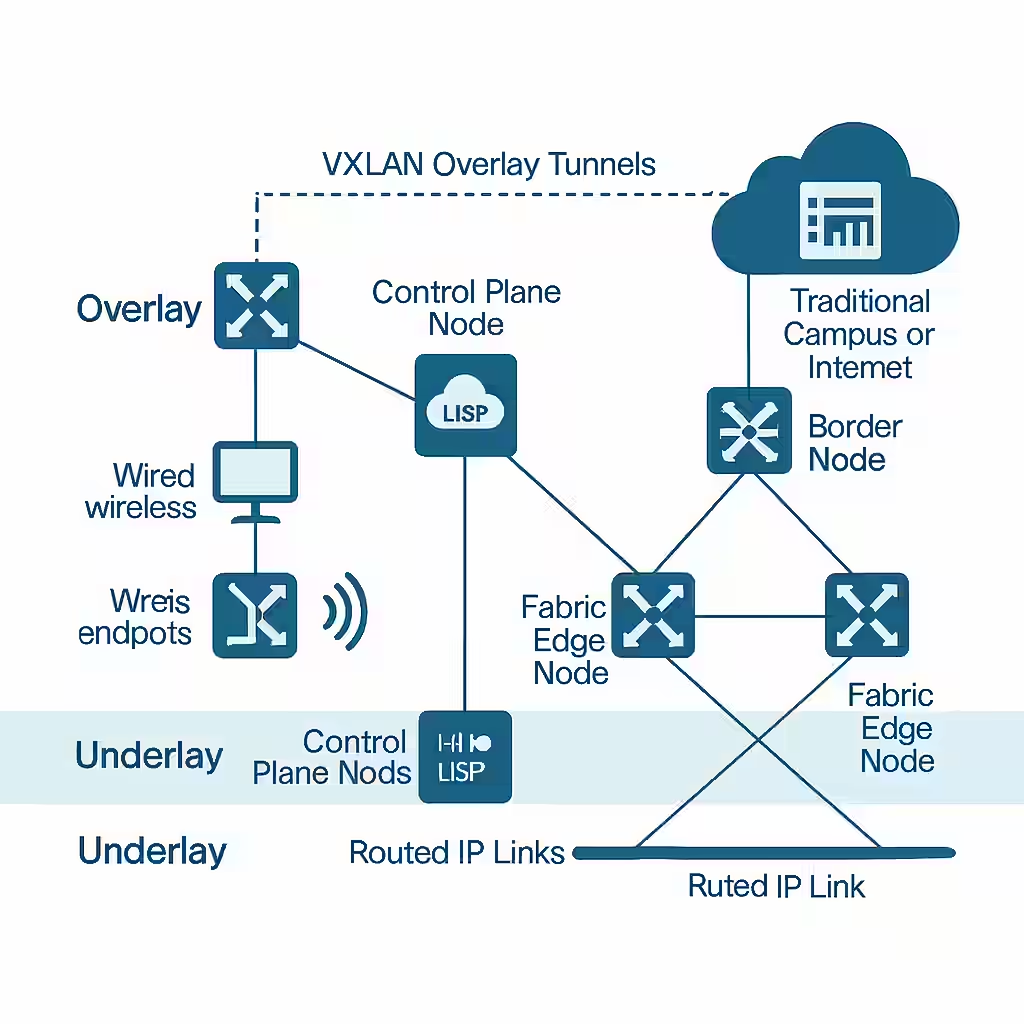
Cisco SD-Access Architecture Explained: The Blueprint for Modern Campus Networks
As enterprise networks evolve, traditional campus architectures often struggle with increasing demands for automation, security, and scalability. Cisco Software-Defined Access (SD-Access) emerges as the answer—a network fabric that reimagines how campus networks are designed, deployed, and managed.
This blog dives into the core concepts of SD-Access, focusing on its architecture, control and data planes, fabric overlays, and the coexistence strategy with traditional networks.
Why SD-Access Is a Paradigm Shift
Conventional campus designs rely heavily on manual configuration, VLAN sprawl, and inefficient access control methods. SD-Access simplifies these by abstracting the underlying network and introducing centralized policy, segmentation, and automation—all powered by Cisco DNA Center.
Key Concepts
SD-Access Architecture Overview
At its core, SD-Access is a fabric-based network model where endpoints are decoupled from their physical locations. It introduces new roles and concepts:
- Underlay: The foundational IP transport network (typically Layer 3), connecting all fabric nodes.
- Overlay: The logical network built on top of the underlay, using tunneling (VXLAN) for segmentation and traffic forwarding.
- Control Plane: A distributed database (LISP-based) that maps user/device identity to their current location.
- Data Plane: VXLAN tunnels that forward encapsulated traffic across the fabric.
Components of the SD-Access Fabric
- Fabric Edge Nodes: Access-layer switches where endpoints connect; they encapsulate traffic into VXLAN.
- Fabric Control Plane Node: Maintains endpoint location information using LISP; enables identity-based routing.
- Fabric Border Node: Acts as the gateway between the SD-Access fabric and external networks (e.g., internet, non-fabric).
- Fabric Wireless Controller: Integrates wireless traffic into the fabric using CAPWAP tunnels from access points.
- DNA Center (DNAC): The central controller for policy, provisioning, and assurance in SD-Access.
Control and Data Plane Deep Dive
Control Plane (LISP – Locator/ID Separation Protocol)
- Maintains a mapping database of Endpoint ID (EID) to Routing Locator (RLOC).
- Enables seamless mobility—users can roam the network while retaining their IP and policy.
Data Plane (VXLAN Tunneling)
- Provides Layer 2 and Layer 3 segmentation via encapsulated traffic.
- Supports scalable group segmentation (SGT) for enforcing policies between different user or device groups.
Overlay Fabric Communication
- When an endpoint connects, the fabric edge node queries the control plane for the destination location.
- Once located, a VXLAN tunnel is built dynamically to the corresponding fabric node for traffic forwarding.
Traditional Campus Network Integration
SD-Access does not demand a rip-and-replace strategy. It can coexist with traditional campus networks:
- Via Border Nodes: The SD-Access fabric connects to legacy Layer 2/Layer 3 domains through the border node, preserving interoperability.
- Shared Services: DNS, DHCP, or internet access can reside outside the fabric but be accessible through policies.
- Staging Migration: Organizations can transition floor-by-floor or building-by-building to SD-Access.
Considerations for Design and Deployment
- Underlay Design: Ensure reliable IP connectivity—often using IS-IS or OSPF.
- Control Plane Redundancy: Deploy multiple control nodes for high availability.
- Segmentation Strategy: Plan VRFs and SGTs early to align with business groups.
- Wireless Integration: Use Fabric Mode WLCs and APs to fully extend the fabric to wireless clients.
- Monitoring: Leverage DNA Center Assurance for deep insights and anomaly detection.
Config Insight: Verifying VXLAN Tunnel on Edge Node
show fabric vn-segmentThis command provides information about VXLAN tunnels and segment IDs on Cisco fabric-enabled switches.
-
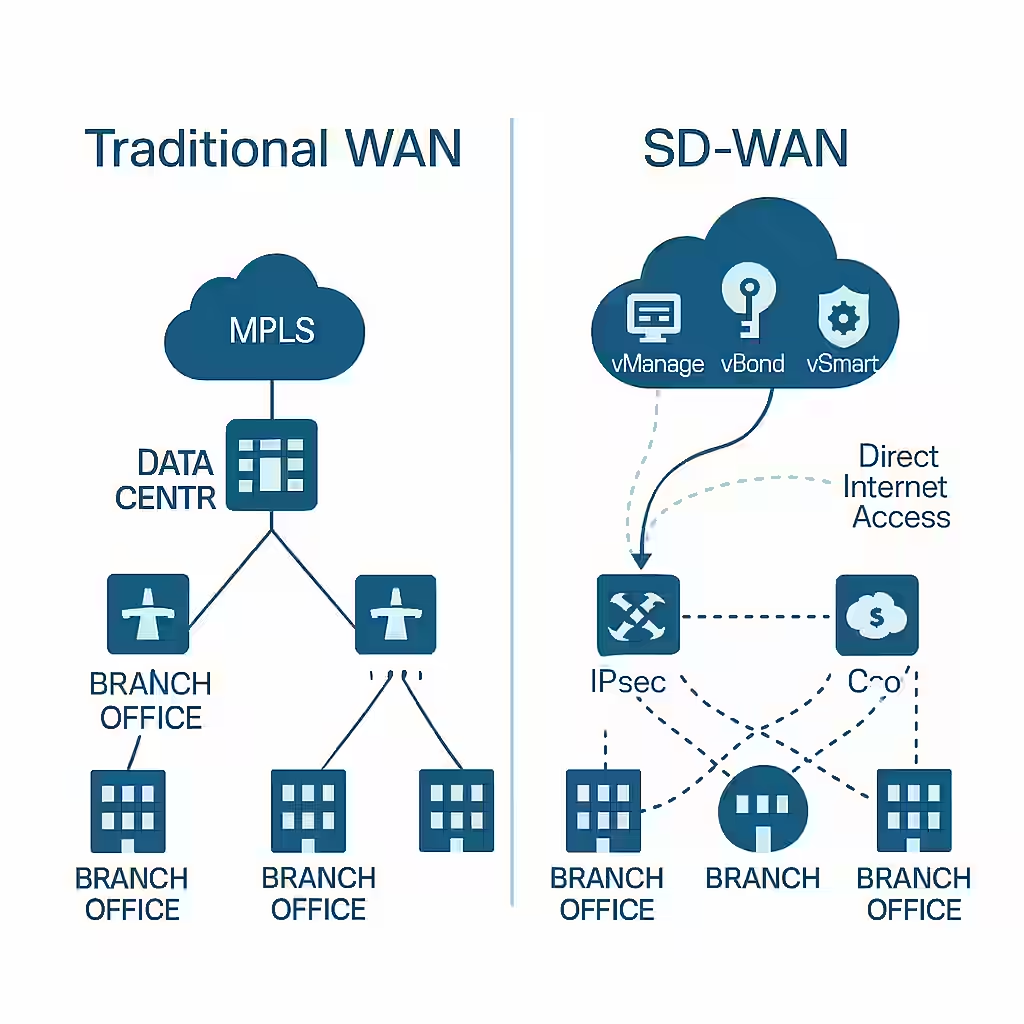
Traditional WAN vs. SD-WAN: A Tale of Two Architectures
The way enterprises connect remote branches to their data centers and applications has dramatically changed. Traditional WANs served well in the era of centralized computing, but as cloud adoption surged, so did the need for a more agile, scalable, and cost-effective solution—enter SD-WAN.
The WAN Evolution
Traditional WANs relied heavily on private circuits like MPLS for site-to-site connectivity. These networks were dependable but expensive, with limited flexibility. Modern businesses now need dynamic access to cloud applications, SaaS platforms, and hybrid environments—all with predictable performance and security.
Key Concepts
Traditional WAN
- Architecture: Hub-and-spoke, where branch offices connect to a central data center via MPLS.
- Routing: Static or manually configured routing policies.
- Traffic Flow: All branch internet traffic is typically backhauled to the data center.
- Management: Device-by-device configuration, often requiring on-site IT support.
- Security: Centralized at the data center, with firewalls and security stacks.
Limitations:
- Costly MPLS circuits
- Poor cloud performance due to backhaul
- Limited visibility and control
- Complex provisioning and scaling
Software-Defined WAN (SD-WAN)
- Architecture: Cloud-first, with direct-to-internet and inter-branch IPsec tunnels.
- Routing: Centralized policy-driven routing via controllers like Cisco vSmart.
- Traffic Flow: Internet-bound traffic can exit directly from the branch (DIA).
- Management: Centralized via GUI dashboards (e.g., Cisco vManage).
- Security: Integrated or cloud-based, with encryption, firewall, and segmentation.
Advantages:
- Cost savings through broadband and LTE use
- Improved cloud access and application performance
- Simplified provisioning with zero-touch deployment
- Granular control with application-aware policies
Side-by-Side Comparison
Feature Traditional WAN SD-WAN Transport Primarily MPLS MPLS, Broadband, LTE Architecture Hub-and-Spoke Cloud-Optimized, Any-to-Any Security Centralized Distributed and Integrated Traffic Handling Backhauled Direct Internet Access (DIA) Provisioning Manual, Complex Zero-Touch Provisioning (ZTP) Policy Control Static Centralized and Dynamic Cloud Integration Limited Native and Optimized
Considerations for Migration
- Business Goals: Cost reduction, cloud readiness, remote work?
- Network Size: Number of branches, cloud dependencies.
- Security Needs: Compliance, segmentation, threat protection.
- IT Skillset: Comfort with centralized management and automation.
Config Insight: SD-WAN Tunnel Verification
show sdwan control connectionsThis command checks the control plane tunnel status on a Cisco SD-WAN edge device.
-

Behind the Scenes of Cisco SD-WAN: Control and Data Planes Demystified
Software-Defined WAN (SD-WAN) is revolutionizing how enterprises connect distributed sites, ensuring performance, security, and flexibility across various transport networks like MPLS, broadband, and LTE. Cisco’s SD-WAN solution goes a step further—integrating cloud-first architecture with enterprise-grade security and centralized control.
Why Cisco SD-WAN Is a Game-Changer
Traditional WANs are rigid and expensive to scale. Cisco SD-WAN separates control from data forwarding, enabling intelligent routing, simplified management, and secure connectivity—even across the public internet. It’s like upgrading from a paper map to a GPS with traffic-aware rerouting.
Key Concepts
Control Plane vs. Data Plane
- Control Plane: Manages routing decisions, topology awareness, and policy enforcement.
- Data Plane: Handles the actual forwarding of user traffic between sites.
In Cisco SD-WAN, these planes are separated and handled by different elements:
SD-WAN Components and Their Roles
1. vSmart Controller (Control Plane)
- Acts as the policy and routing brain of the SD-WAN fabric.
- Distributes control and security policies to WAN edge devices.
- Uses secure connections (DTLS/TLS) to communicate with edge devices.
2. vBond Orchestrator (Authentication and Orchestration)
- The first point of contact for all SD-WAN components.
- Authenticates WAN edge devices (using certificates) and helps them discover vSmart and vManage.
- Ensures proper NAT traversal for devices behind firewalls.
3. vManage NMS (Network Management System)
- Central GUI dashboard for configuration, monitoring, and troubleshooting.
- Pushes configurations and policies to all SD-WAN devices.
- Supports zero-touch provisioning (ZTP).
4. WAN Edge Routers (Data Plane)
- Also called Cisco SD-WAN routers or vEdge/Catalyst Edge.
- Forward traffic based on policies and topology from the vSmart controller.
- Build secure IPsec tunnels with other edge devices.
How It All Works Together
- Device Onboarding: WAN edge devices authenticate via vBond and register with vManage and vSmart.
- Policy Distribution: vSmart pushes control and data policies to the WAN edge routers.
- Tunnel Formation: Edge devices establish IPsec tunnels with each other using information from vSmart.
- Traffic Forwarding: Data flows directly between sites using the optimal path as determined by policy.
Considerations for Design
- Redundancy: Deploy multiple controllers (vSmart, vBond, vManage) for HA.
- Scalability: Cloud-hosted controllers scale easily with enterprise growth.
- Security: End-to-end encryption via IPsec tunnels.
- Cloud Integration: Direct connections to SaaS/IaaS platforms using Cloud OnRamp.
Config Insight: vEdge Control Connection Verification
vEdge# show control connectionsThis command confirms if the vEdge router is securely connected to vSmart and vBond controllers.
-
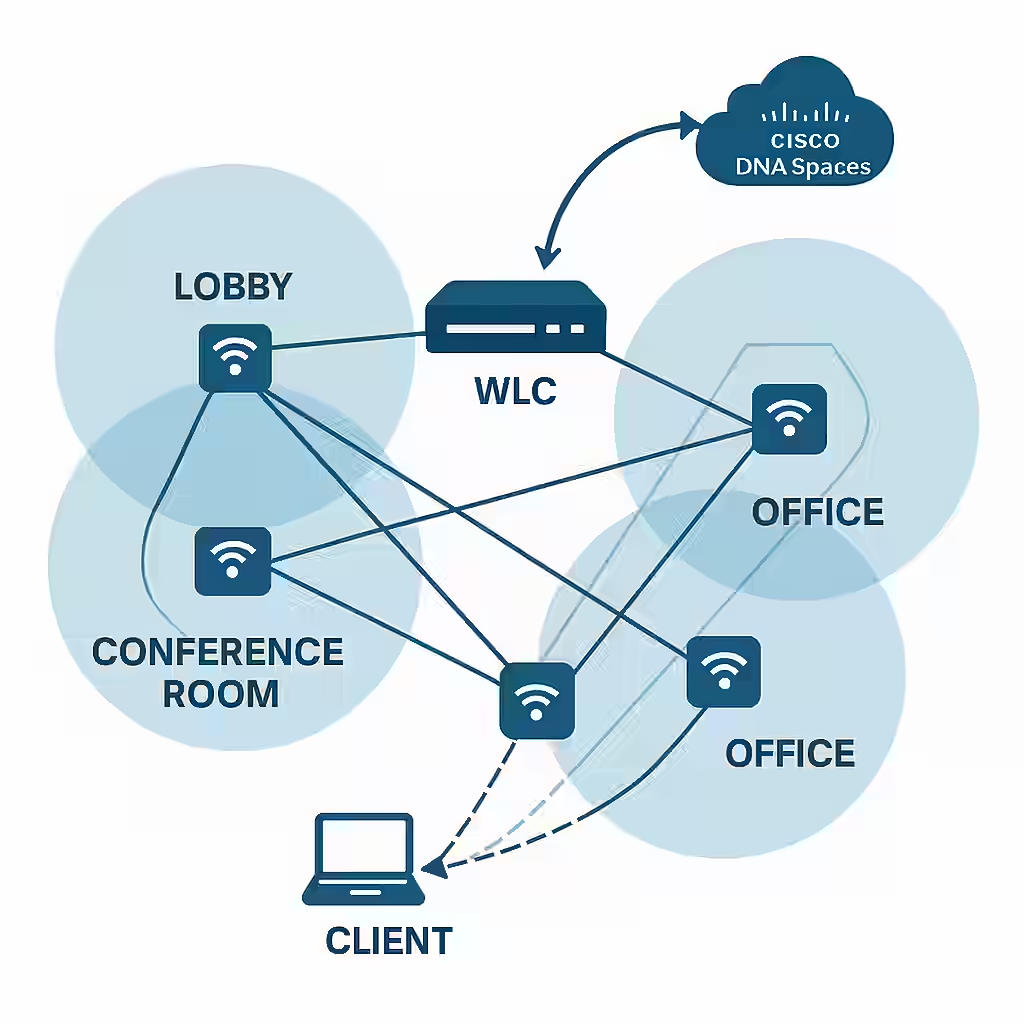
Pinpointing Precision: Understanding Location Services in WLAN Design
Wi-Fi is no longer just about internet access—it’s about intelligence. Modern wireless LANs (WLANs) do more than connect devices; they can track their location. Location services have become a powerful tool in environments like healthcare, retail, manufacturing, and even smart campuses, providing insights into movement, usage, and security.
Why Location Services Matter
Knowing where a device is within a building can improve safety, enhance customer experience, and streamline operations. From tracking assets in hospitals to pushing promotions in retail stores, WLAN-based location services unlock a new layer of network value.
Key Concepts
1. Types of WLAN Location Services
- Presence: Detects if a device is in the area—basic, but useful for foot traffic analysis.
- Zone-Based Location: Identifies general areas or zones where a device is located (e.g., lobby, office).
- XY Location (Real-Time Location Services or RTLS): Tracks exact coordinates within a space.
- Z-Axis (Vertical Positioning): Determines floor level in multistory buildings.
2. Technologies Behind Location Services
- RSSI (Received Signal Strength Indicator): Measures signal strength from APs to estimate proximity. Simple but affected by walls and interference.
- TDoA (Time Difference of Arrival): Measures time for signals to reach multiple APs to triangulate position. More accurate but requires tight synchronization.
- Angle of Arrival (AoA): Uses antenna arrays to calculate direction of the signal. High precision in newer deployments.
- BLE (Bluetooth Low Energy): Often used in conjunction with Wi-Fi for hyperlocal accuracy.
3. Location Engines and Platforms
- Cisco DNA Spaces: Offers presence analytics, location heat maps, behavior patterns, and integration with business applications.
- Cisco CMX (Connected Mobile Experiences): Legacy platform for location tracking and analytics.
Considerations for WLAN Location Design
- Access Point Density: Minimum of 3 APs in range for accurate triangulation.
- AP Placement: Uniform spacing and low mounting height improve precision.
- Calibration: Perform RF fingerprinting for higher accuracy, especially in RTLS.
- Device Type Awareness: Different devices report RSSI differently—consider in tuning.
- Privacy and Compliance: Implement policies that align with data protection regulations.
Config Insight: Enabling Location Services on a Cisco WLC
wlc# config location enable wlc# config location history enableNote: Advanced location features typically require integration with Cisco DNA Spaces or CMX.
-
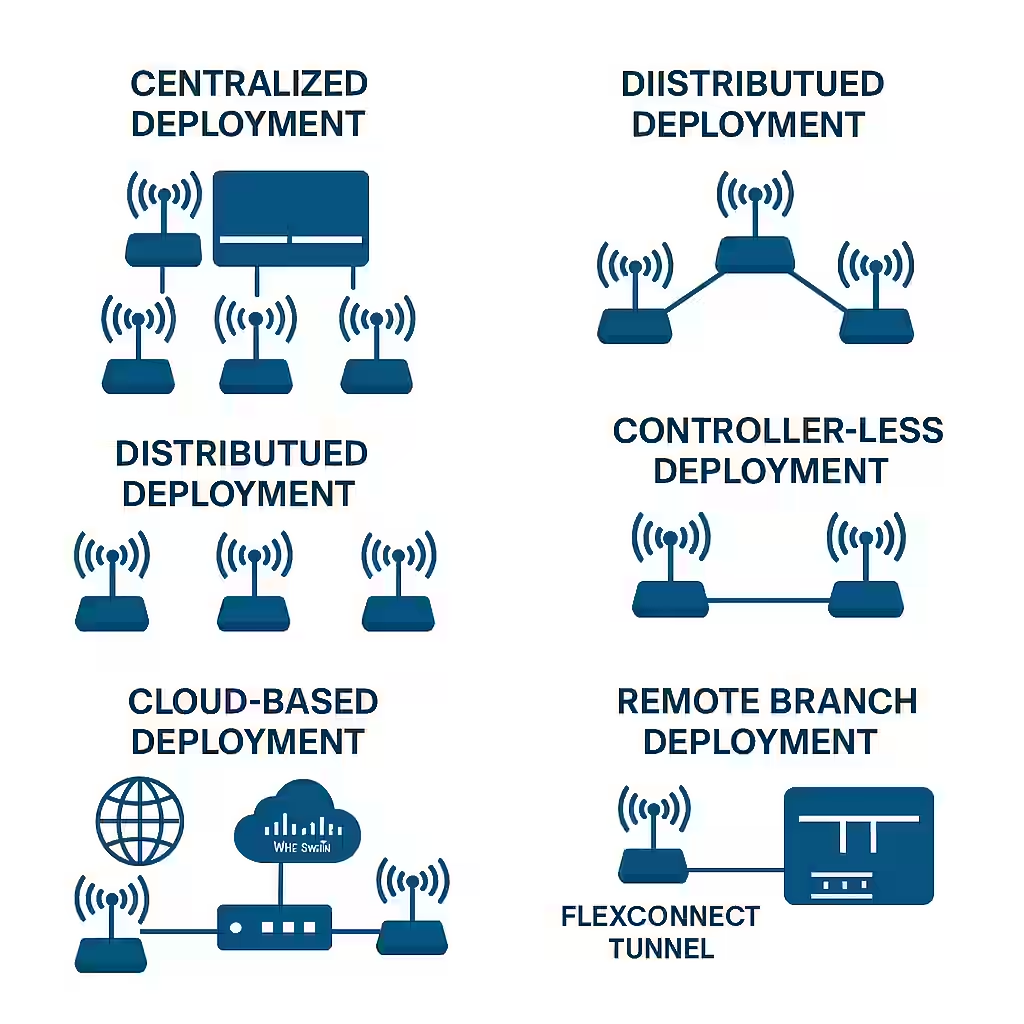
Choosing the Right Wireless Deployment Model: Centralized, Distributed, Cloud, and More
Wireless networks are no longer optional—they’re essential. But not all wireless setups are created equal. Depending on the size, location, and goals of a business, the right deployment model can drastically improve performance, manageability, and scalability. Understanding the strengths and use cases of different wireless deployment models is key to designing a robust network.
Why Wireless Deployment Models Matter
Selecting the wrong wireless architecture can lead to poor coverage, scalability issues, and difficult management. A proper model ensures better performance, centralized control, and optimized costs based on the organization’s needs.
Key Concepts
Centralized (Controller-Based) Deployment
All access points (APs) forward traffic and control functions to a central Wireless LAN Controller (WLC). The WLC manages configurations, security, and policies.- Ideal for: Medium to large campus networks
- Benefits: Centralized management, scalability, policy consistency
- Drawback: Controller is a single point of failure without redundancy
Distributed (Autonomous) Deployment
Each AP operates independently, making its own decisions and handling management and data forwarding locally.- Ideal for: Small offices or isolated deployments
- Benefits: Simple setup, no need for central controller
- Drawback: Difficult to manage at scale, lacks centralized control
Controller-Less (Mobility Express or Embedded WLC)
An AP takes on the role of a controller for a small group of APs, combining the benefits of centralized and autonomous deployments.- Ideal for: Small to mid-sized businesses
- Benefits: Centralized-like management without dedicated WLC
- Drawback: Limited scalability
Cloud-Based Deployment
APs connect to a cloud-managed platform (e.g., Cisco Meraki), which handles configuration, monitoring, and updates.- Ideal for: Multi-site businesses, retail chains
- Benefits: Easy remote management, reduced on-site IT needs
- Drawback: Requires reliable internet connectivity
Remote Branch Deployment
Designed for branch offices connected to a central hub, often using FlexConnect or SD-Branch solutions. Local switching is available even if WAN fails.- Ideal for: Branch offices with limited IT resources
- Benefits: Central control, local resiliency
- Drawback: Complex WAN dependency if not configured properly
Considerations When Choosing a Model
- Scale: How many APs and locations are needed?
- Control: Is centralized management essential?
- Resiliency: What happens during WAN outages?
- IT Resources: Is there staff available for on-site management?
- Cost: Budget for hardware, licenses, and ongoing support
Config Insight: Basic AP Registration with Controller
AP# capwap ap controller ip address 192.168.100.10 -
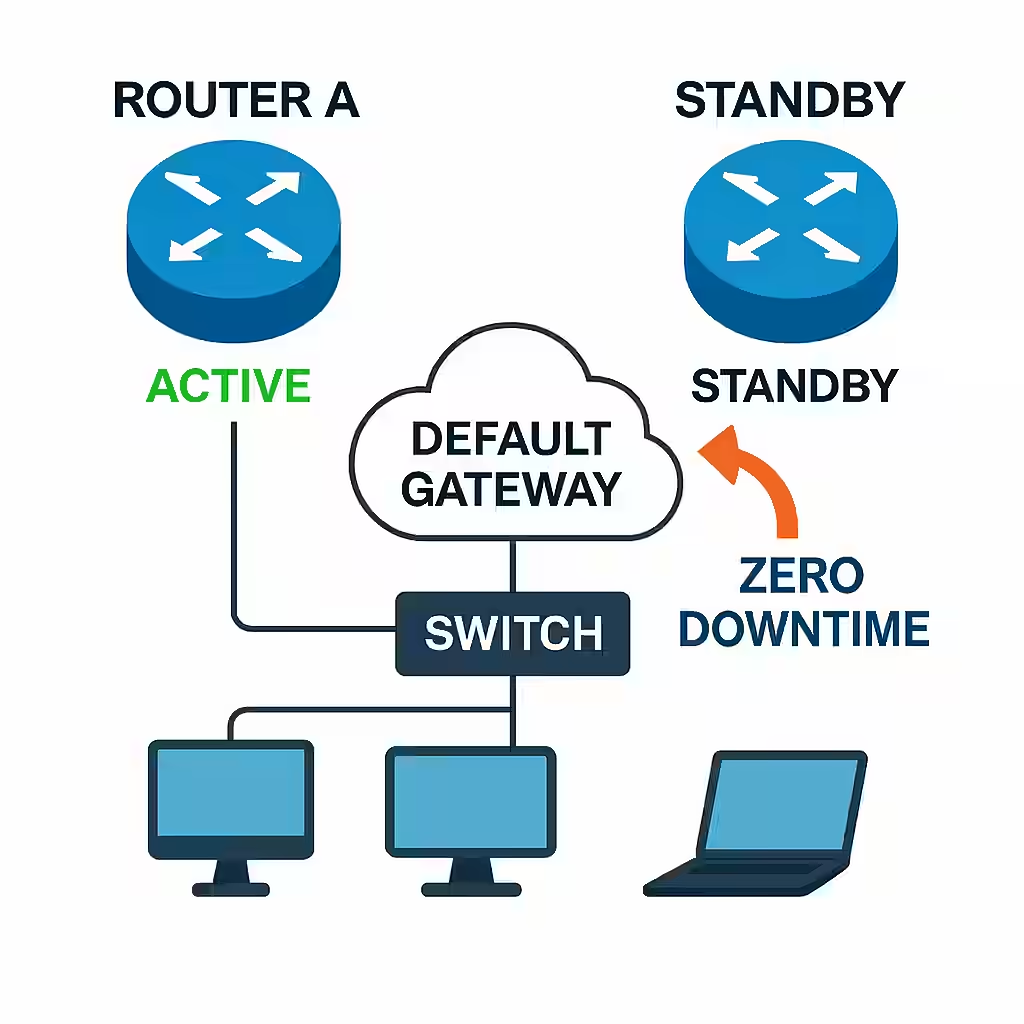
Never Down Again: Mastering High Availability with Redundancy, FHRP, and SSO
Downtime is the nemesis of modern enterprise networks. Whether it’s caused by hardware failure, software bugs, or human error, even a few minutes of network outage can disrupt operations and cost businesses real money. High availability (HA) techniques aim to eliminate single points of failure and ensure uninterrupted network services.
What Makes a Network “Highly Available”?
High availability doesn’t just mean having extra equipment—it’s about designing the network so that if one component fails, others can instantly take over without disruption. This is done using a combination of physical and logical redundancy, failover protocols, and software enhancements.
Key Concepts
Redundancy
Redundancy involves deploying duplicate network elements—like routers, switches, links, and power supplies—to serve as backups in case of failure.- Link Redundancy: Multiple uplinks prevent isolation of network segments.
- Device Redundancy: Backup routers or switches ensure uninterrupted routing and switching.
- Path Redundancy: Multiple data paths maintain connectivity if one route fails.
First Hop Redundancy Protocol (FHRP)
End devices rely on a default gateway for outbound traffic. If that gateway fails, without FHRP, traffic halts. FHRP introduces a virtual IP address shared between two or more routers.- HSRP (Hot Standby Router Protocol) – Cisco proprietary, uses an active/standby model.
- VRRP (Virtual Router Redundancy Protocol) – Open standard, similar to HSRP.
- GLBP (Gateway Load Balancing Protocol) – Cisco proprietary, offers load balancing and redundancy.
Stateful Switchover (SSO)
SSO enables a router or switch with dual route processors to seamlessly switch from a failed active processor to a standby one without interrupting traffic.- Function: Synchronizes configuration and forwarding information between processors.
- Use Case: Most effective in modular switches and high-end routers with redundant supervisors.
Considerations for Implementing High Availability
- Critical Path Identification: Focus HA designs on links and devices that handle essential traffic.
- Failover Time: Minimize downtime by using fast convergence protocols and SSO.
- Load Sharing: Where possible, use GLBP or similar methods to balance traffic across redundant paths.
- Cost vs. Benefit: High availability often requires more hardware—ensure it aligns with business impact and budget.
- Maintenance: Plan for software upgrades and changes without full network outages.
Config Sample: HSRP Basic Setup
interface GigabitEthernet0/1 ip address 192.168.10.2 255.255.255.0 standby 1 ip 192.168.10.1 standby 1 priority 110 standby 1 preempt -
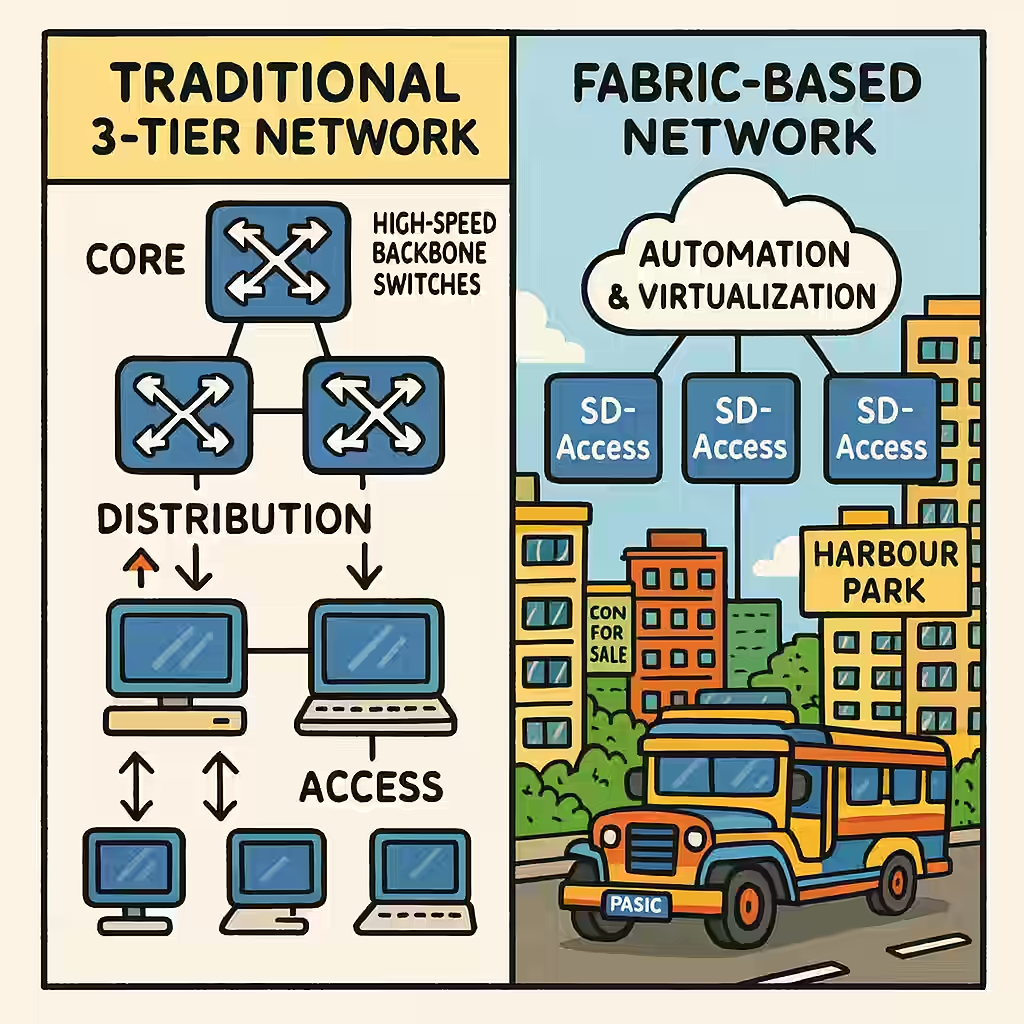
Mastering Enterprise Network Design: Tier 2, Tier 3, and Fabric Capacity Planning
When businesses scale up, their network infrastructure must evolve just as quickly. A simple flat network might work for a startup, but it often crumbles under the weight of growing user demands, applications, and devices. This is where structured enterprise network designs—Tier 2, Tier 3, and Fabric—play a crucial role, along with proactive capacity planning.
Why Network Design Matters
Enterprise networks, much like urban road systems, need thoughtful planning to handle growing traffic. A well-architected network improves performance, supports scalability, ensures reliability, and makes troubleshooting significantly easier. Without a clear design, bottlenecks and outages can quickly disrupt operations.
Understanding Tier 2, Tier 3, and Fabric Designs
Tier 2 (Collapsed Core Architecture):
Ideal for small to medium enterprises, this design merges the core and distribution layers into one. It’s simple and cost-effective, reducing the number of devices and overall complexity.- Strengths: Lower cost, easier deployment and management.
- Limitations: Less redundancy, scalability constraints.
Tier 3 (Traditional Hierarchical Design):
Best suited for larger networks, this model divides the architecture into three layers: Access, Distribution, and Core.- Access Layer: Connects end-user devices to the network.
- Distribution Layer: Aggregates traffic and enforces policies.
- Core Layer: High-speed backbone that connects distribution layers.
- Strengths: Excellent scalability, fault tolerance, and modularity.
- Limitations: Higher infrastructure and maintenance costs.
Fabric Design (Software-Defined Access – SD-Access):
The most modern approach, fabric-based architecture virtualizes the network and introduces automation and centralized management.- Strengths: Policy consistency, segmentation, scalability, automation.
- Limitations: Requires deeper expertise and investment.
Key Considerations for Capacity Planning
Effective capacity planning ensures the network can support both current demands and future growth. Poor planning often leads to bandwidth shortages, hardware strain, and user dissatisfaction.
- Growth Forecasting: Estimate future users, devices, and application needs.
- Traffic Analysis: Account for peak usage periods, not just daily averages.
- Redundancy: Implement failover options at critical points.
- Uplink Optimization: Ensure trunk links can handle aggregate traffic.
- Physical Resources: Consider power, space, and cooling needs.
- Scalability: Choose equipment and topologies that allow for easy expansion.
Config Sample: Setting Up VLAN Access and Trunk Ports
interface FastEthernet0/1 switchport mode access switchport access vlan 10 spanning-tree portfast interface GigabitEthernet0/1 switchport trunk encapsulation dot1q switchport mode trunk -
A Network-Centric Dive into MS Server Basics
Hey there, future Microsoft server wizards! If you’re prepping for the AZ-800 exam (Administering Windows Server Hybrid Core Infrastructure), you’re about to embark on a thrilling journey into the heart of Microsoft’s server ecosystem. This blog is your trusty guide, written in a network-centric style to make core concepts like Active Directory (AD), DNS, Organizational Units (OUs), domains, trees, forests, objects, and more not just understandable but downright fun. Think of this as your cheat sheet for acing the exam, served with a side of enthusiasm and a sprinkle of humor. Let’s dive into the networked wonderland of Windows Server!
The Big Picture: Why Windows Server and Networking Go Hand in Hand
Windows Server is the backbone of enterprise IT, and at its core, it’s all about networks. Whether you’re managing users, securing resources, or ensuring systems talk to each other seamlessly, networking is the glue that holds it all together. The AZ-800 exam tests your ability to administer Windows Server in hybrid environments (on-premises and cloud), so understanding how networking ties into concepts like Active Directory and DNS is non-negotiable. Let’s break it down with a network-centric lens, exploring how these components work together to create a robust, scalable IT environment.
Imagine a bustling city where data packets are cars, servers are skyscrapers, and Active Directory is the city hall keeping everything organized. Ready to tour this city? Let’s go!
Active Directory (AD): The Heart of Identity Management
What Is It?
Active Directory is like the ultimate Rolodex for your network. It’s a directory service that stores information about objects (users, computers, printers, etc.) and makes it easy to manage access, authentication, and authorization across your network. Think of AD as the gatekeeper who knows everyone’s name, job, and who they’re allowed to talk to.
Why It’s Network-Centric
AD relies on your network to function. It uses protocols like LDAP (Lightweight Directory Access Protocol) and Kerberos to communicate between servers, clients, and other devices. Without a solid network, AD would be like a librarian shouting book titles into the void—no one would hear her.
Key Components for AZ-800
- Objects: These are the “things” AD manages—users, groups, computers, printers, etc. Each object has attributes (e.g., a user’s name, email, or password). For the exam, know that objects are the building blocks of AD.
- Domains: A domain is a logical group of objects (like a department in our city analogy). It’s a management boundary where policies and security settings are applied. For example,
contoso.comcould be a domain. - Organizational Units (OUs): OUs are like folders within a domain. They let you organize objects (e.g., all HR users in one OU) and apply specific policies (Group Policy Objects, or GPOs) to them. OUs are your go-to for keeping things tidy and manageable.
- Trees: A tree is a collection of domains that share a common namespace. For example,
hr.contoso.comandsales.contoso.comare domains in the same tree because they share thecontoso.comroot. - Forests: A forest is the top-level container, a collection of trees that share a common schema and trust relationships. Think of it as a country with multiple states (trees). A forest is the ultimate security and administrative boundary.
- Trusts: These are network relationships that allow domains or forests to share resources. For example, a trust between
contoso.comandfabrikam.comlets users from one domain access resources in another. Trusts rely on network connectivity to authenticate users across domains.
Exam Tip
For AZ-800, understand how AD integrates with hybrid environments. You’ll need to know how to sync on-premises AD with Azure AD (now Microsoft Entra ID) using tools like Azure AD Connect. Also, brush up on managing trusts and troubleshooting replication issues across networks.
Fun Fact: AD was introduced with Windows 2000 Server—yep, it’s been keeping networks organized for over two decades!
DNS: The Phonebook of Your Network
What Is It?
The Domain Name System (DNS) is the internet’s phonebook, translating human-friendly names (like
www.contoso.com) into IP addresses (like192.168.1.10) that computers understand. In a Windows Server environment, DNS is critical for AD to function because AD uses DNS to locate domain controllers and services.Why It’s Network-Centric
DNS is the ultimate network matchmaker. Without it, devices wouldn’t know how to find each other. AD relies on DNS records (like SRV records) to point clients to domain controllers. If DNS fails, your network is like a party where no one knows anyone’s name—chaos ensues.
Key DNS Concepts for AZ-800
- Zones: These are containers for DNS records. A forward lookup zone maps names to IP addresses, while a reverse lookup zone does the opposite. For example, the zone
contoso.comholds all records for that domain. - Records: These are the entries in the DNS database. Common ones include:
- A (Address): Maps a hostname to an IPv4 address.
- AAAA: Maps a hostname to an IPv6 address.
- SRV (Service): Points to services like domain controllers.
- CNAME (Canonical Name): An alias for another hostname.
- AD-Integrated Zones: These store DNS data in AD, making it more secure and enabling replication across domain controllers. This is a big deal for AZ-800, as it ties DNS tightly to AD’s network infrastructure.
- Conditional Forwarders: These tell your DNS server where to send queries for specific domains. For example, if you need to resolve
fabrikam.com, a conditional forwarder points to Fabrikam’s DNS server.
Exam Tip
Know how to troubleshoot DNS issues (e.g., using
nslookupordig) and configure DNS in hybrid scenarios, like setting up DNS for Azure-based resources. Also, understand how DNS supports AD replication across sites.Fun Analogy: DNS is like a GPS for your network. Without it, your data packets would be driving around aimlessly, asking for directions.
Domains, Trees, and Forests: Building Your Network Hierarchy
Let’s zoom out and look at how AD organizes your network into a hierarchy. This is where domains, trees, and forests come together to create a scalable, manageable structure.
- Domains: As mentioned, a domain is a logical group of objects. It’s like a department in a company—self-contained but part of a larger organization. Domains use DNS names (e.g.,
contoso.com) and rely on network connectivity to communicate with clients and other domains. - Trees: Multiple domains with a shared namespace form a tree. For example,
contoso.com,hr.contoso.com, andsales.contoso.comform a tree. Trees are great for organizations with multiple divisions that need to share resources but maintain separate management. - Forests: A forest is the top dog, containing one or more trees. It’s the ultimate boundary for security, replication, and schema. Forests are network-intensive because domain controllers in different domains or trees need to replicate data (like user accounts) across the network.
Why It Matters for Networking
This hierarchy depends on network links for Hawkins’ Law (a fundamental AD principle) states that domain controllers must be reachable via DNS and network connectivity. If your network is slow or misconfigured, replication between domain controllers can fail, causing chaos (e.g., users unable to log in). For AZ-800, you’ll need to know how to configure sites and subnets to optimize replication over wide area networks (WANs).
Fun Fact: A forest can have multiple domains, but they all share a single schema—the blueprint for what kinds of objects AD can store. Mess up the schema, and you’ve got a network-wide headache!
Organizational Units (OUs): Keeping Your Network Tidy
OUs are like the Marie Kondo of Active Directory—they help you organize objects so your network “sparks joy.” You can group users, computers, or other objects into OUs and apply specific policies (GPOs) to them. For example, you might have an OU for the IT department with strict password policies and another for interns with looser settings.
Network Connection
OUs rely on network connectivity to apply GPOs to clients. If a client can’t reach a domain controller due to a network issue, it won’t get the latest policies, which could lead to security or configuration problems.
Exam Tip
For AZ-800, know how to create and manage OUs, delegate administrative control (e.g., letting the HR team manage their own OU), and troubleshoot GPO application issues across networks.
Fun Analogy: OUs are like playlists on your music app—grouping songs (objects) by genre (department) so you can apply the right vibe (policies) to each.
Group Policy Objects (GPOs): The Network’s Rulebook
GPOs are the policies you apply to OUs, domains, or sites to enforce settings like password requirements, desktop backgrounds, or software installations. They’re network-dependent because clients need to contact domain controllers to download and apply GPOs.
Key Points for AZ-800
- Scope: GPOs can apply to sites, domains, or OUs. Site-based GPOs are useful for network-specific settings, like directing clients to the nearest domain controller.
- Troubleshooting: If a GPO isn’t applying, check network connectivity, DNS resolution, and the client’s ability to reach a domain controller. Tools like
gpresultorrsop.mscare your friends here.
Fun Fact: GPOs are like the network’s mom, telling everyone to clean their room (or update their passwords) whether they like it or not.
Sites and Subnets: Optimizing for Network Performance
AD sites and subnets are all about making your network efficient. A site represents a physical location (e.g., a branch office) with good network connectivity (usually a LAN). A subnet is the IP address range for that site (e.g.,
192.168.1.0/24).Why It’s Network-Centric
Sites and subnets tell AD which domain controllers are closest to clients, reducing latency and bandwidth usage. For example, if a user in New York logs in, AD should direct them to a New York domain controller, not one in Tokyo. Misconfigured sites can lead to slow logins or replication issues.
Exam Tip
For AZ-800, know how to configure sites, associate subnets with them, and manage inter-site replication (e.g., using Site Links and Bridgehead Servers). Understand how to monitor replication with tools like
repadmin.Fun Analogy: Sites are like choosing the closest coffee shop to your office—you don’t want to trek across town (or a slow WAN link) for your latte.
Objects: The Building Blocks of AD
Objects are the entities AD manages—users, computers, groups, printers, etc. Each has attributes (e.g., a user’s phone number or a computer’s operating system). Objects are stored in the AD database and replicated across domain controllers via the network.
Network Connection
Objects are only useful if clients can access them. If DNS fails or network links are down, users can’t authenticate, and computers can’t join the domain. For AZ-800, know how to manage objects (e.g., creating users with PowerShell) and troubleshoot access issues.
Fun Fact: The AD database (NTDS.dit) is like a giant spreadsheet of your network’s objects, and it’s replicated to every domain controller to ensure consistency.
Hybrid Networking: Bridging On-Prem and Cloud
The AZ-800 exam emphasizes hybrid environments, where on-premises AD integrates with Azure AD (Microsoft Entra ID). This requires network connectivity between your local servers and Azure, often via VPNs or ExpressRoute.
Key Tools
- Azure AD Connect: Syncs on-premises AD objects to Azure AD, enabling single sign-on (SSO) and cloud access.
- Conditional Access: Policies in Azure AD that control access based on network conditions (e.g., requiring multi-factor authentication for external networks).
Exam Tip
Understand how to configure Azure AD Connect, troubleshoot sync issues, and secure hybrid network connections. Know the role of DNS in resolving Azure AD endpoints.
Fun Analogy: Hybrid AD is like a dual-citizenship passport—your users can move seamlessly between on-premises and cloud networks with the right credentials.
Troubleshooting: When the Network Goes Haywire
Networks aren’t perfect, and AZ-800 will test your ability to fix issues. Common problems include:
- DNS Failures: Clients can’t find domain controllers. Use
nslookupor check DNS server logs. - Replication Issues: Domain controllers aren’t syncing. Use
repadmin /replsummaryto diagnose. - GPO Failures: Policies aren’t applying. Check network connectivity and use
gpresult /r. - Slow Logins: Could be site/subnet misconfiguration or WAN bottlenecks. Verify site links and network performance.
Fun Tip: Troubleshooting is like being a network detective—follow the clues (logs, error codes) to catch the culprit!
Wrapping It Up: Your AZ-800 Network Adventure
Mastering Windows Server for the AZ-800 exam is all about understanding how AD, DNS, OUs, domains, trees, forests, and objects work together over a network. Think of your network as a living, breathing ecosystem where every component relies on connectivity to function. By focusing on the network-centric aspects—DNS resolution, replication, site configuration, and hybrid integration—you’ll be ready to tackle the exam and manage real-world environments like a pro.
So, study hard, keep your network cables untangled, and go ace that AZ-800 exam! If you have specific topics you want to dive deeper into, let me know, and I’ll whip up a follow-up with more details. Happy networking.
