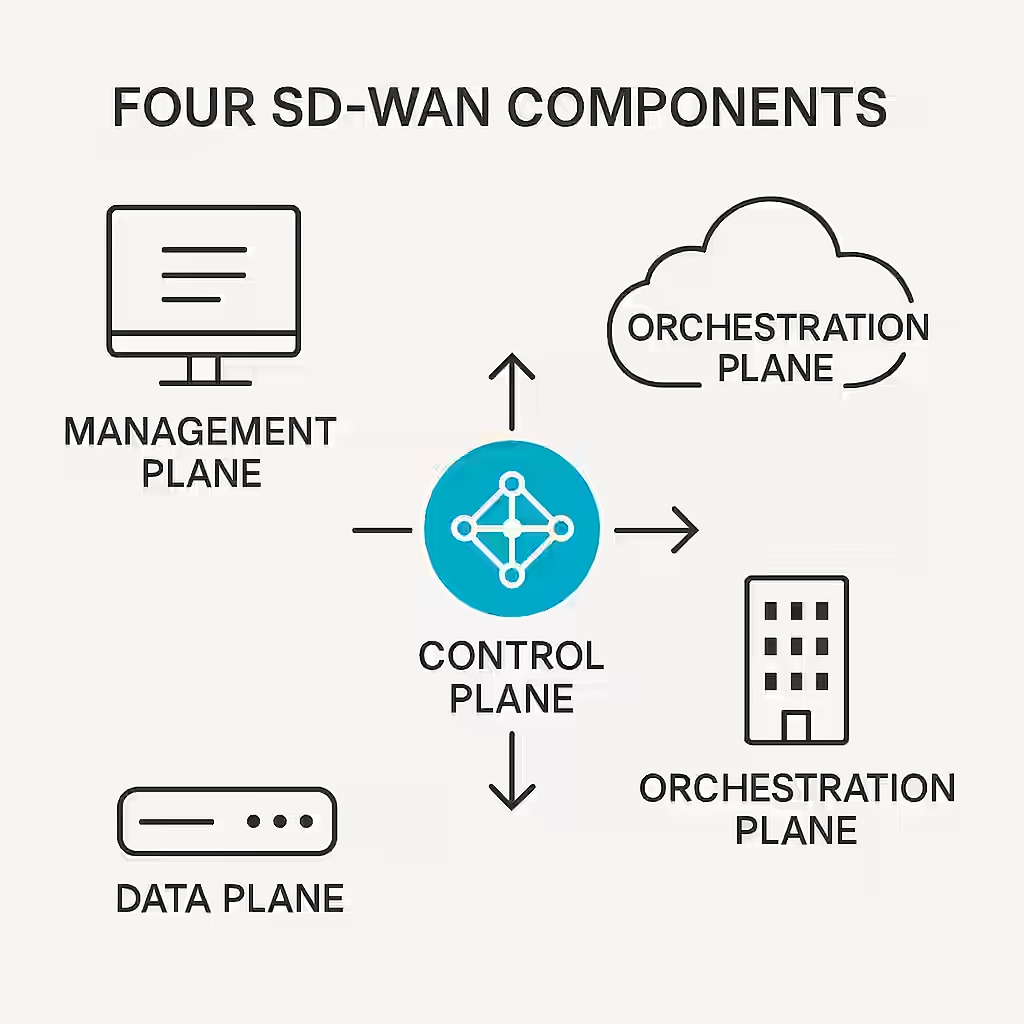
Now that we’ve met the building blocks of Cisco SD-WAN, it’s time to dig deeper into how they work together to create a seamless, secure network. At the heart of SD-WAN lies the dynamic interplay between the control plane and data plane—two sides of the same coin that ensure data travels efficiently, securely, and intelligently.
The control plane is the mastermind behind the scenes, orchestrated by the vSmart controllers. It’s responsible for distributing routing information using the Overlay Management Protocol (OMP). OMP shares three types of routes: OMP routes, TLOC routes, and service routes. Think of OMP as the language spoken by all SD-WAN components, ensuring they’re always in sync, no matter how far apart.
Each branch office or site connects to the SD-WAN fabric through a WAN edge device, which registers itself with the vSmart controller. This registration is like checking in at a secure airport—vSmart verifies the device’s identity and ensures it’s authorized to join the network. Once onboard, vSmart tells each edge device how to reach any other branch or data center securely and efficiently.
While the control plane handles routing decisions, the data plane is where data actually flows. It’s responsible for building encrypted tunnels between devices and forwarding traffic along the best path. Cisco SD-WAN uses IPsec to protect data in transit, ensuring that sensitive information is always secure.
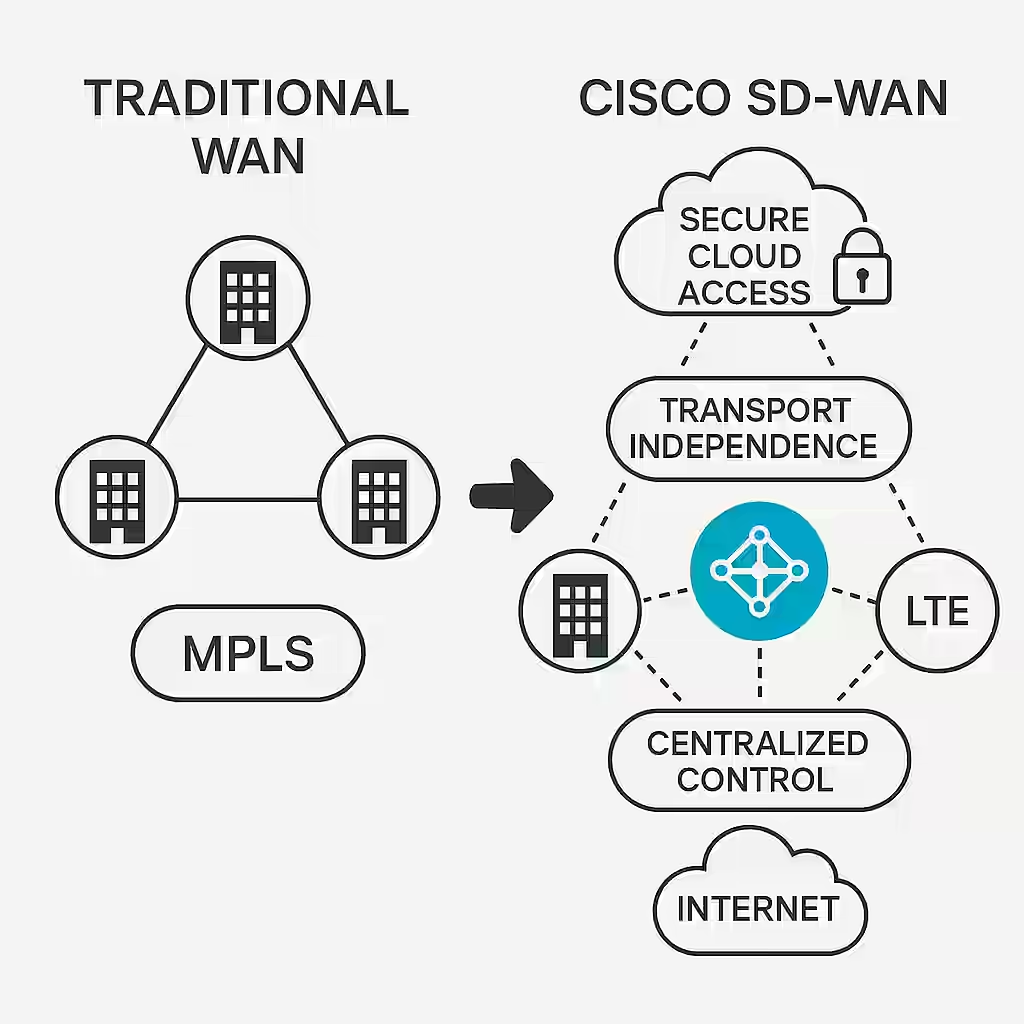
But the data plane isn’t just about encryption. It’s also about performance. TLOC (Transport Location) routes define how data should travel across multiple transport types—MPLS, broadband, or LTE. This is where transport independence shines, giving businesses the freedom to use the best available path at any moment.
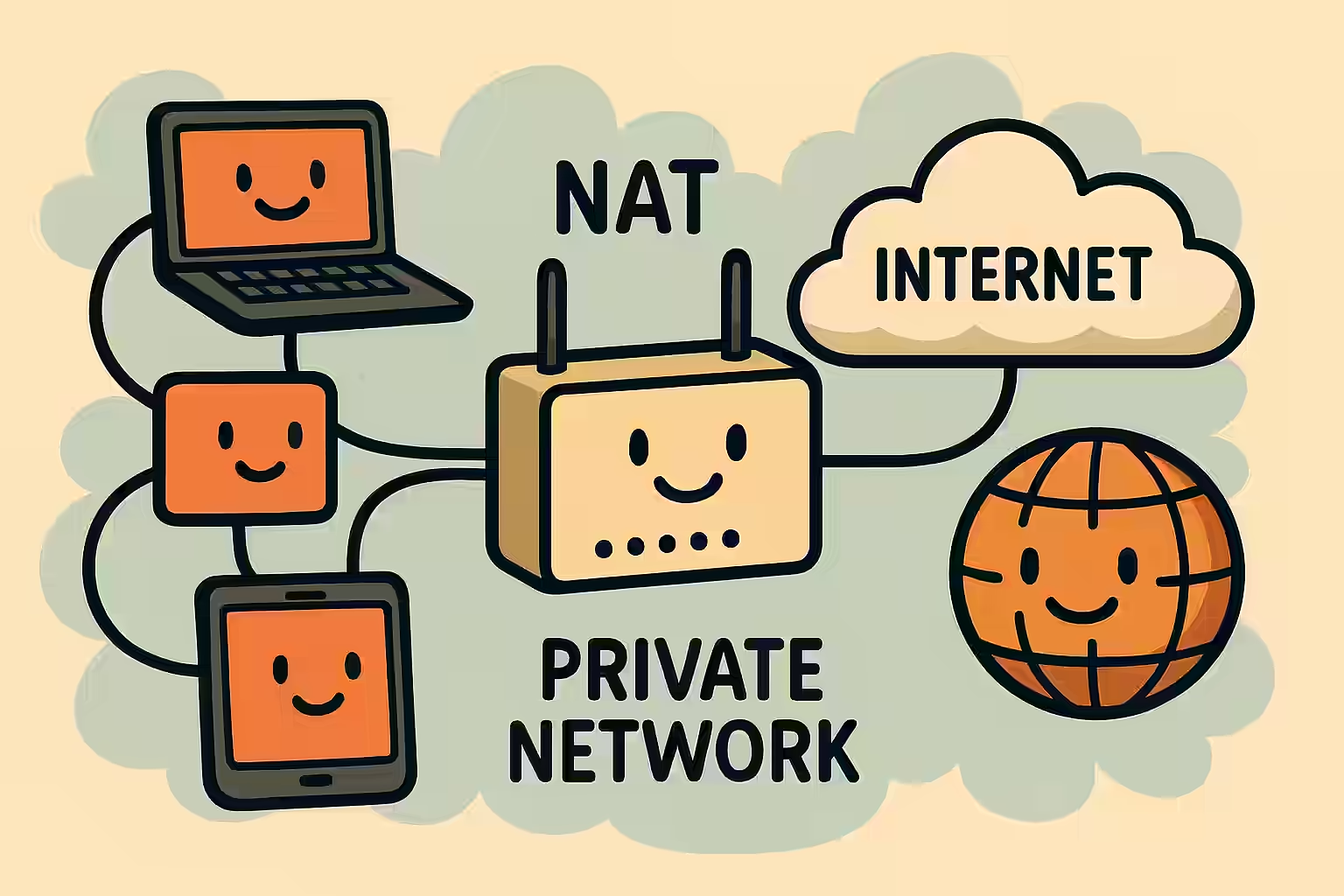
Understanding NAT behavior is also critical in the data plane. Cisco SD-WAN supports Full Cone NAT, Symmetric NAT, Address Restricted Cone NAT, and Port Restricted Cone NAT, ensuring data can navigate through firewalls and NAT devices without a hitch.
Here’s a command that helps verify the control and data plane operations:
show sdwan omp routesThis command shows you the OMP routes shared across the fabric—your window into the routing intelligence of SD-WAN.
- What protocol does the control plane use to distribute routing information?
Answer: Overlay Management Protocol (OMP). - What are the three types of OMP routes?
Answer: OMP routes, TLOC routes, and service routes. - How does the data plane ensure secure traffic forwarding?
Answer: It uses IPsec encryption for tunnels. - What is transport independence in the context of TLOC routes?
Answer: The ability to use different transport types (MPLS, LTE, broadband) seamlessly. - Name one type of NAT behavior supported by Cisco SD-WAN.
Answer: Full Cone NAT, Symmetric NAT, Address Restricted Cone NAT, or Port Restricted Cone NAT.