Sometimes, defeat comes even when someone gives their best—and it hurts. But defeat has a way of teaching humility. It reminds us that not every closed door is a failure, but a redirection. The job that didn’t choose them isn’t the end of the road. It’s a step toward something better, something more aligned. Stay humble, stay ready, and keep moving forward. #StayHopeful
Category: Blog
-
A Network-Centric Dive into MS Server Basics
Hey there, future Microsoft server wizards! If you’re prepping for the AZ-800 exam (Administering Windows Server Hybrid Core Infrastructure), you’re about to embark on a thrilling journey into the heart of Microsoft’s server ecosystem. This blog is your trusty guide, written in a network-centric style to make core concepts like Active Directory (AD), DNS, Organizational Units (OUs), domains, trees, forests, objects, and more not just understandable but downright fun. Think of this as your cheat sheet for acing the exam, served with a side of enthusiasm and a sprinkle of humor. Let’s dive into the networked wonderland of Windows Server!
The Big Picture: Why Windows Server and Networking Go Hand in Hand
Windows Server is the backbone of enterprise IT, and at its core, it’s all about networks. Whether you’re managing users, securing resources, or ensuring systems talk to each other seamlessly, networking is the glue that holds it all together. The AZ-800 exam tests your ability to administer Windows Server in hybrid environments (on-premises and cloud), so understanding how networking ties into concepts like Active Directory and DNS is non-negotiable. Let’s break it down with a network-centric lens, exploring how these components work together to create a robust, scalable IT environment.
Imagine a bustling city where data packets are cars, servers are skyscrapers, and Active Directory is the city hall keeping everything organized. Ready to tour this city? Let’s go!
Active Directory (AD): The Heart of Identity Management
What Is It?
Active Directory is like the ultimate Rolodex for your network. It’s a directory service that stores information about objects (users, computers, printers, etc.) and makes it easy to manage access, authentication, and authorization across your network. Think of AD as the gatekeeper who knows everyone’s name, job, and who they’re allowed to talk to.
Why It’s Network-Centric
AD relies on your network to function. It uses protocols like LDAP (Lightweight Directory Access Protocol) and Kerberos to communicate between servers, clients, and other devices. Without a solid network, AD would be like a librarian shouting book titles into the void—no one would hear her.
Key Components for AZ-800
- Objects: These are the “things” AD manages—users, groups, computers, printers, etc. Each object has attributes (e.g., a user’s name, email, or password). For the exam, know that objects are the building blocks of AD.
- Domains: A domain is a logical group of objects (like a department in our city analogy). It’s a management boundary where policies and security settings are applied. For example,
contoso.comcould be a domain. - Organizational Units (OUs): OUs are like folders within a domain. They let you organize objects (e.g., all HR users in one OU) and apply specific policies (Group Policy Objects, or GPOs) to them. OUs are your go-to for keeping things tidy and manageable.
- Trees: A tree is a collection of domains that share a common namespace. For example,
hr.contoso.comandsales.contoso.comare domains in the same tree because they share thecontoso.comroot. - Forests: A forest is the top-level container, a collection of trees that share a common schema and trust relationships. Think of it as a country with multiple states (trees). A forest is the ultimate security and administrative boundary.
- Trusts: These are network relationships that allow domains or forests to share resources. For example, a trust between
contoso.comandfabrikam.comlets users from one domain access resources in another. Trusts rely on network connectivity to authenticate users across domains.
Exam Tip
For AZ-800, understand how AD integrates with hybrid environments. You’ll need to know how to sync on-premises AD with Azure AD (now Microsoft Entra ID) using tools like Azure AD Connect. Also, brush up on managing trusts and troubleshooting replication issues across networks.
Fun Fact: AD was introduced with Windows 2000 Server—yep, it’s been keeping networks organized for over two decades!
DNS: The Phonebook of Your Network
What Is It?
The Domain Name System (DNS) is the internet’s phonebook, translating human-friendly names (like
www.contoso.com) into IP addresses (like192.168.1.10) that computers understand. In a Windows Server environment, DNS is critical for AD to function because AD uses DNS to locate domain controllers and services.Why It’s Network-Centric
DNS is the ultimate network matchmaker. Without it, devices wouldn’t know how to find each other. AD relies on DNS records (like SRV records) to point clients to domain controllers. If DNS fails, your network is like a party where no one knows anyone’s name—chaos ensues.
Key DNS Concepts for AZ-800
- Zones: These are containers for DNS records. A forward lookup zone maps names to IP addresses, while a reverse lookup zone does the opposite. For example, the zone
contoso.comholds all records for that domain. - Records: These are the entries in the DNS database. Common ones include:
- A (Address): Maps a hostname to an IPv4 address.
- AAAA: Maps a hostname to an IPv6 address.
- SRV (Service): Points to services like domain controllers.
- CNAME (Canonical Name): An alias for another hostname.
- AD-Integrated Zones: These store DNS data in AD, making it more secure and enabling replication across domain controllers. This is a big deal for AZ-800, as it ties DNS tightly to AD’s network infrastructure.
- Conditional Forwarders: These tell your DNS server where to send queries for specific domains. For example, if you need to resolve
fabrikam.com, a conditional forwarder points to Fabrikam’s DNS server.
Exam Tip
Know how to troubleshoot DNS issues (e.g., using
nslookupordig) and configure DNS in hybrid scenarios, like setting up DNS for Azure-based resources. Also, understand how DNS supports AD replication across sites.Fun Analogy: DNS is like a GPS for your network. Without it, your data packets would be driving around aimlessly, asking for directions.
Domains, Trees, and Forests: Building Your Network Hierarchy
Let’s zoom out and look at how AD organizes your network into a hierarchy. This is where domains, trees, and forests come together to create a scalable, manageable structure.
- Domains: As mentioned, a domain is a logical group of objects. It’s like a department in a company—self-contained but part of a larger organization. Domains use DNS names (e.g.,
contoso.com) and rely on network connectivity to communicate with clients and other domains. - Trees: Multiple domains with a shared namespace form a tree. For example,
contoso.com,hr.contoso.com, andsales.contoso.comform a tree. Trees are great for organizations with multiple divisions that need to share resources but maintain separate management. - Forests: A forest is the top dog, containing one or more trees. It’s the ultimate boundary for security, replication, and schema. Forests are network-intensive because domain controllers in different domains or trees need to replicate data (like user accounts) across the network.
Why It Matters for Networking
This hierarchy depends on network links for Hawkins’ Law (a fundamental AD principle) states that domain controllers must be reachable via DNS and network connectivity. If your network is slow or misconfigured, replication between domain controllers can fail, causing chaos (e.g., users unable to log in). For AZ-800, you’ll need to know how to configure sites and subnets to optimize replication over wide area networks (WANs).
Fun Fact: A forest can have multiple domains, but they all share a single schema—the blueprint for what kinds of objects AD can store. Mess up the schema, and you’ve got a network-wide headache!
Organizational Units (OUs): Keeping Your Network Tidy
OUs are like the Marie Kondo of Active Directory—they help you organize objects so your network “sparks joy.” You can group users, computers, or other objects into OUs and apply specific policies (GPOs) to them. For example, you might have an OU for the IT department with strict password policies and another for interns with looser settings.
Network Connection
OUs rely on network connectivity to apply GPOs to clients. If a client can’t reach a domain controller due to a network issue, it won’t get the latest policies, which could lead to security or configuration problems.
Exam Tip
For AZ-800, know how to create and manage OUs, delegate administrative control (e.g., letting the HR team manage their own OU), and troubleshoot GPO application issues across networks.
Fun Analogy: OUs are like playlists on your music app—grouping songs (objects) by genre (department) so you can apply the right vibe (policies) to each.
Group Policy Objects (GPOs): The Network’s Rulebook
GPOs are the policies you apply to OUs, domains, or sites to enforce settings like password requirements, desktop backgrounds, or software installations. They’re network-dependent because clients need to contact domain controllers to download and apply GPOs.
Key Points for AZ-800
- Scope: GPOs can apply to sites, domains, or OUs. Site-based GPOs are useful for network-specific settings, like directing clients to the nearest domain controller.
- Troubleshooting: If a GPO isn’t applying, check network connectivity, DNS resolution, and the client’s ability to reach a domain controller. Tools like
gpresultorrsop.mscare your friends here.
Fun Fact: GPOs are like the network’s mom, telling everyone to clean their room (or update their passwords) whether they like it or not.
Sites and Subnets: Optimizing for Network Performance
AD sites and subnets are all about making your network efficient. A site represents a physical location (e.g., a branch office) with good network connectivity (usually a LAN). A subnet is the IP address range for that site (e.g.,
192.168.1.0/24).Why It’s Network-Centric
Sites and subnets tell AD which domain controllers are closest to clients, reducing latency and bandwidth usage. For example, if a user in New York logs in, AD should direct them to a New York domain controller, not one in Tokyo. Misconfigured sites can lead to slow logins or replication issues.
Exam Tip
For AZ-800, know how to configure sites, associate subnets with them, and manage inter-site replication (e.g., using Site Links and Bridgehead Servers). Understand how to monitor replication with tools like
repadmin.Fun Analogy: Sites are like choosing the closest coffee shop to your office—you don’t want to trek across town (or a slow WAN link) for your latte.
Objects: The Building Blocks of AD
Objects are the entities AD manages—users, computers, groups, printers, etc. Each has attributes (e.g., a user’s phone number or a computer’s operating system). Objects are stored in the AD database and replicated across domain controllers via the network.
Network Connection
Objects are only useful if clients can access them. If DNS fails or network links are down, users can’t authenticate, and computers can’t join the domain. For AZ-800, know how to manage objects (e.g., creating users with PowerShell) and troubleshoot access issues.
Fun Fact: The AD database (NTDS.dit) is like a giant spreadsheet of your network’s objects, and it’s replicated to every domain controller to ensure consistency.
Hybrid Networking: Bridging On-Prem and Cloud
The AZ-800 exam emphasizes hybrid environments, where on-premises AD integrates with Azure AD (Microsoft Entra ID). This requires network connectivity between your local servers and Azure, often via VPNs or ExpressRoute.
Key Tools
- Azure AD Connect: Syncs on-premises AD objects to Azure AD, enabling single sign-on (SSO) and cloud access.
- Conditional Access: Policies in Azure AD that control access based on network conditions (e.g., requiring multi-factor authentication for external networks).
Exam Tip
Understand how to configure Azure AD Connect, troubleshoot sync issues, and secure hybrid network connections. Know the role of DNS in resolving Azure AD endpoints.
Fun Analogy: Hybrid AD is like a dual-citizenship passport—your users can move seamlessly between on-premises and cloud networks with the right credentials.
Troubleshooting: When the Network Goes Haywire
Networks aren’t perfect, and AZ-800 will test your ability to fix issues. Common problems include:
- DNS Failures: Clients can’t find domain controllers. Use
nslookupor check DNS server logs. - Replication Issues: Domain controllers aren’t syncing. Use
repadmin /replsummaryto diagnose. - GPO Failures: Policies aren’t applying. Check network connectivity and use
gpresult /r. - Slow Logins: Could be site/subnet misconfiguration or WAN bottlenecks. Verify site links and network performance.
Fun Tip: Troubleshooting is like being a network detective—follow the clues (logs, error codes) to catch the culprit!
Wrapping It Up: Your AZ-800 Network Adventure
Mastering Windows Server for the AZ-800 exam is all about understanding how AD, DNS, OUs, domains, trees, forests, and objects work together over a network. Think of your network as a living, breathing ecosystem where every component relies on connectivity to function. By focusing on the network-centric aspects—DNS resolution, replication, site configuration, and hybrid integration—you’ll be ready to tackle the exam and manage real-world environments like a pro.
So, study hard, keep your network cables untangled, and go ace that AZ-800 exam! If you have specific topics you want to dive deeper into, let me know, and I’ll whip up a follow-up with more details. Happy networking.
-

Navigating the Control and Data Plane in Cisco SD-WAN
Now that we’ve met the building blocks of Cisco SD-WAN, it’s time to dig deeper into how they work together to create a seamless, secure network. At the heart of SD-WAN lies the dynamic interplay between the control plane and data plane—two sides of the same coin that ensure data travels efficiently, securely, and intelligently.
The control plane is the mastermind behind the scenes, orchestrated by the vSmart controllers. It’s responsible for distributing routing information using the Overlay Management Protocol (OMP). OMP shares three types of routes: OMP routes, TLOC routes, and service routes. Think of OMP as the language spoken by all SD-WAN components, ensuring they’re always in sync, no matter how far apart.
Each branch office or site connects to the SD-WAN fabric through a WAN edge device, which registers itself with the vSmart controller. This registration is like checking in at a secure airport—vSmart verifies the device’s identity and ensures it’s authorized to join the network. Once onboard, vSmart tells each edge device how to reach any other branch or data center securely and efficiently.
While the control plane handles routing decisions, the data plane is where data actually flows. It’s responsible for building encrypted tunnels between devices and forwarding traffic along the best path. Cisco SD-WAN uses IPsec to protect data in transit, ensuring that sensitive information is always secure.
But the data plane isn’t just about encryption. It’s also about performance. TLOC (Transport Location) routes define how data should travel across multiple transport types—MPLS, broadband, or LTE. This is where transport independence shines, giving businesses the freedom to use the best available path at any moment.
Understanding NAT behavior is also critical in the data plane. Cisco SD-WAN supports Full Cone NAT, Symmetric NAT, Address Restricted Cone NAT, and Port Restricted Cone NAT, ensuring data can navigate through firewalls and NAT devices without a hitch.
Here’s a command that helps verify the control and data plane operations:
show sdwan omp routesThis command shows you the OMP routes shared across the fabric—your window into the routing intelligence of SD-WAN.
- What protocol does the control plane use to distribute routing information?
Answer: Overlay Management Protocol (OMP). - What are the three types of OMP routes?
Answer: OMP routes, TLOC routes, and service routes. - How does the data plane ensure secure traffic forwarding?
Answer: It uses IPsec encryption for tunnels. - What is transport independence in the context of TLOC routes?
Answer: The ability to use different transport types (MPLS, LTE, broadband) seamlessly. - Name one type of NAT behavior supported by Cisco SD-WAN.
Answer: Full Cone NAT, Symmetric NAT, Address Restricted Cone NAT, or Port Restricted Cone NAT.
- What protocol does the control plane use to distribute routing information?
-
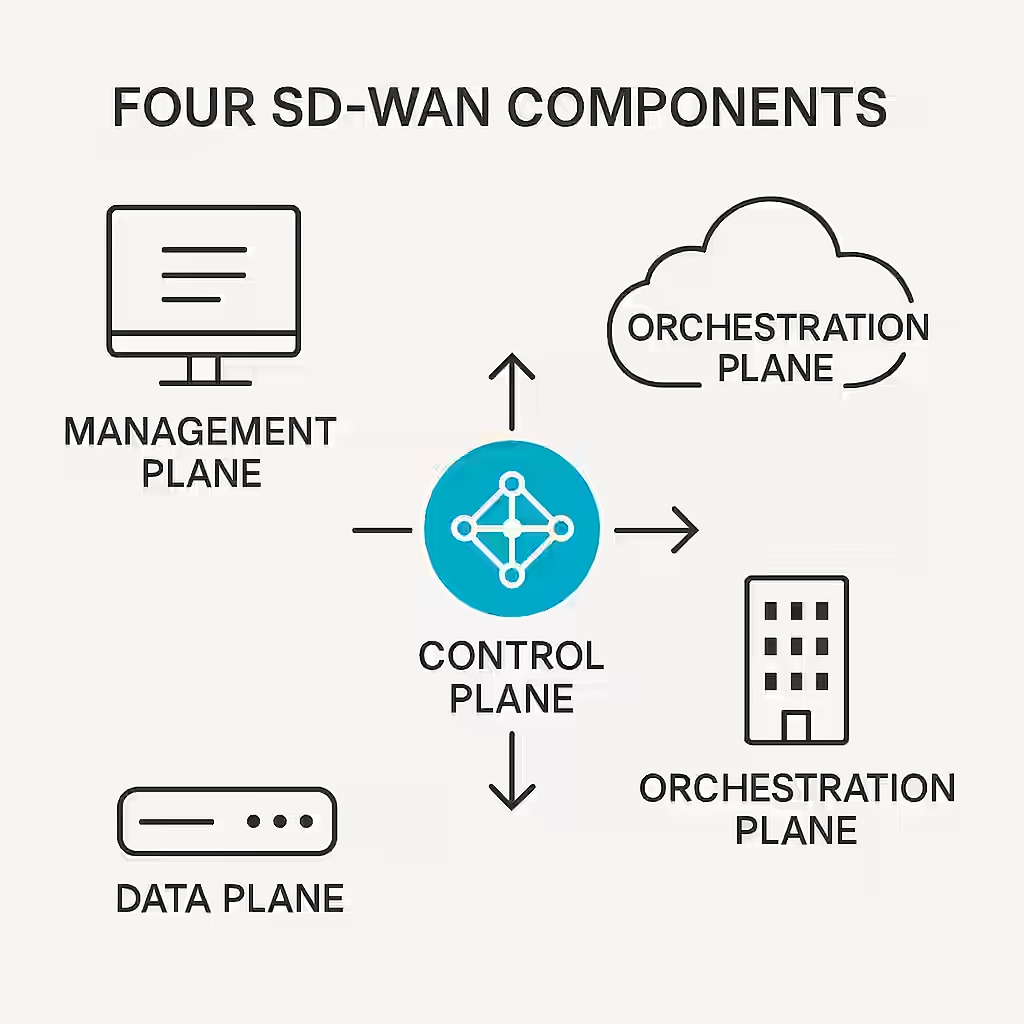
Cisco SD-WAN Components: Building Blocks of a Modern WAN
Every masterpiece needs a solid foundation, and Cisco SD-WAN is no exception. At the heart of this powerful solution lies a set of components, each playing a crucial role in shaping how data flows, how policies are enforced, and how networks are managed. Let’s take a journey through the four pillars that form the backbone of Cisco SD-WAN: the data plane, control plane, management plane, and orchestration plane.
Picture your SD-WAN network as a well-oiled machine. The data plane is where the action happens—traffic flows from branch to data center, to cloud applications, and beyond. It’s here that tunnels are built, encrypted, and data securely finds its way to the right destination. The data plane’s key player? The WAN edge devices, known as vEdge or cEdge routers.
Above the data plane sits the control plane, orchestrated by the vSmart controllers. These act like air traffic control, managing routes, sharing updates, and ensuring that data finds the most efficient and secure path. They’re the brains of the operation, leveraging the Overlay Management Protocol (OMP) to distribute routing information throughout the fabric.
Overseeing it all is the management plane, embodied by Cisco vManage. Think of it as the command center, a single dashboard that provides a panoramic view of your entire network. From here, you can deploy policies, monitor performance, and troubleshoot issues in real time. No more jumping between tools or devices—vManage centralizes everything.
Then there’s the orchestration plane, represented by vBond orchestrators. This component is the gatekeeper, responsible for authenticating all devices before they join the SD-WAN fabric. vBond ensures that only trusted components become part of your network, establishing secure control connections.
Cisco SD-WAN’s architecture is built with scalability in mind. It can handle multi-tenancy, allowing service providers to deliver managed SD-WAN services to different customers on shared infrastructure. It can also be deployed in a variety of ways—on-premises, in the cloud, or as a hybrid model—to fit your unique business needs.
Before you dive in, consider your deployment model: will you leverage vEdge devices or opt for Cisco’s cEdge, built on the ISR/ASR platforms? Will you deploy everything on-premises, or lean on the cloud for flexibility and scale? These decisions will shape your journey and your ability to deliver on the promise of a modern WAN.
Here’s a sneak peek at a verification command that becomes invaluable as you explore the different SD-WAN components:
show sdwan deviceThis command displays the list of all devices in the SD-WAN fabric, giving you quick insight into how your environment is coming together.
- What is the primary role of the data plane in SD-WAN?
Answer: It forwards and encrypts data traffic between sites and applications. - Which SD-WAN component manages the control plane and handles routing updates?
Answer: vSmart controllers. - What is the main function of vManage?
Answer: It acts as the centralized management dashboard for monitoring and configuration. - How does vBond contribute to SD-WAN security?
Answer: It authenticates devices before they join the SD-WAN fabric. - What deployment options are available for SD-WAN?
Answer: On-premises, cloud, or hybrid deployment models.
- What is the primary role of the data plane in SD-WAN?
-
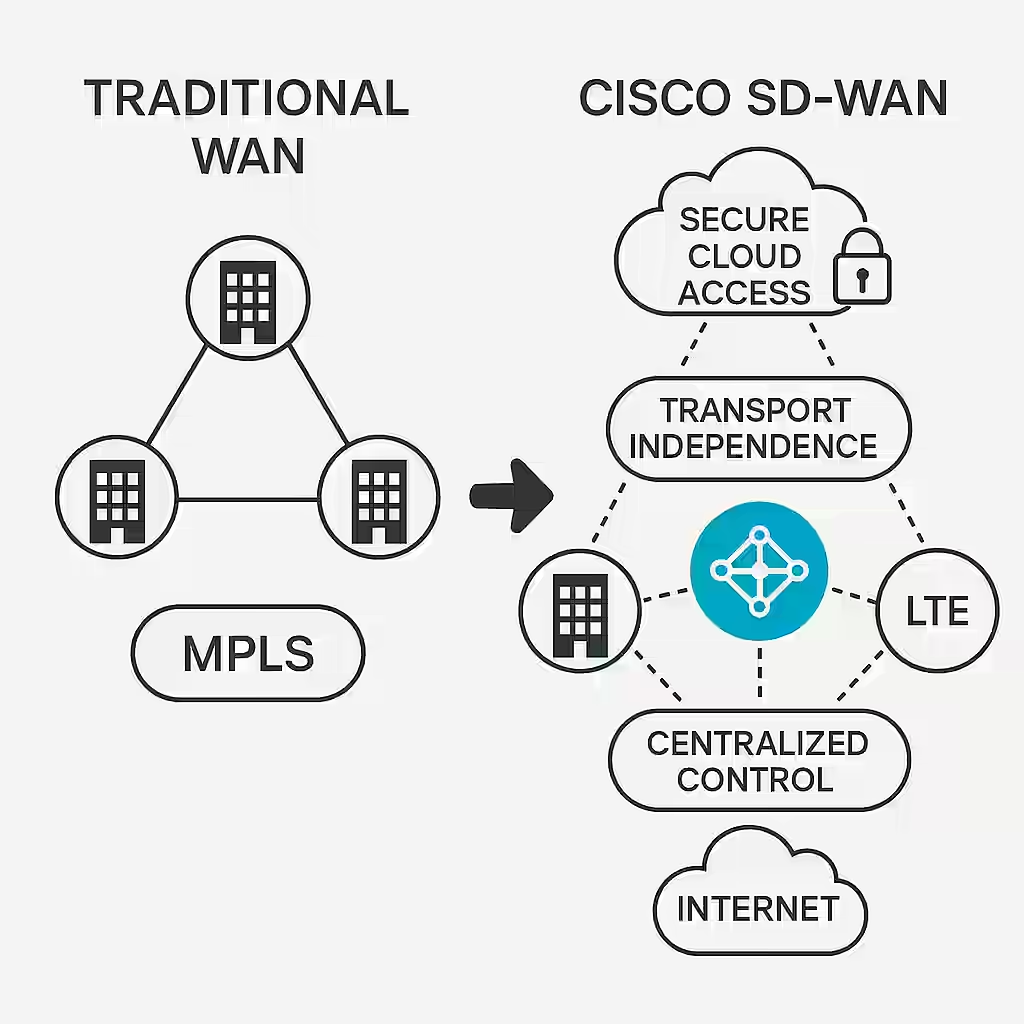
The Evolution of Wide-Area Networks: Cisco SD-WAN Unveiled
The world of networking has undergone a dramatic transformation. In the past, Wide-Area Networks (WANs) were rigid, expensive, and complex—heavily dependent on MPLS circuits and static routing. Today, businesses face a new reality: cloud applications, a remote workforce, and evolving security threats. Enter Cisco SD-WAN, a game-changing technology that brings flexibility, agility, and intelligence to the WAN. Let’s explore how this modern approach is revolutionizing enterprise networking.
Imagine an enterprise with dozens, even hundreds of branches, each struggling to securely and efficiently connect to cloud applications and data centers. Traditional WANs simply can’t keep up with the demand for speed and reliability. Cisco SD-WAN changes the game by decoupling the control plane from the data plane, creating a powerful software-driven architecture. It introduces centralized management, making it easier to orchestrate traffic, enforce policies, and ensure optimal application performance.
But it’s not just about technology. It’s about solving real-world problems. With SD-WAN, businesses can finally achieve the elusive balance between cost and performance. MPLS costs are slashed, replaced by hybrid networks that use broadband and LTE, without compromising security. Critical applications are prioritized, so video calls don’t stutter, and cloud apps stay responsive.
A concept called “multidomain” ties it all together—integrating data centers, branches, and the cloud into a cohesive, secure network. This enables businesses to evolve without fear, leveraging a modern WAN that’s ready for anything.
Before deploying SD-WAN, it’s crucial to assess your current environment. What applications drive your business? How do you want to prioritize them? Are you ready to move from traditional MPLS-only networks to a hybrid approach that leverages multiple transports? Cisco SD-WAN delivers a direct internet access (DIA) capability that ensures cloud applications perform flawlessly, no matter where your users are. ROI becomes more than a buzzword; it’s a measurable outcome of reduced circuit costs and smarter traffic management.
Security remains paramount. Cisco SD-WAN encrypts data end-to-end and uses segmentation to keep sensitive data safe. This is a WAN built for a cloud-first world.
Let’s look at a command that becomes essential in SD-WAN implementation:
show sdwan control connectionsThis command verifies the control connections between SD-WAN devices (like vEdge or cEdge routers) and the controllers, ensuring the architecture is working as designed.
- What challenge does Cisco SD-WAN solve for modern businesses?
Answer: It addresses the need for secure, flexible, and efficient WAN connectivity for cloud apps and remote users. - What does “transport independence” allow?
Answer: It allows the use of multiple transport types (MPLS, LTE, broadband) seamlessly. - Why is centralized management so critical in SD-WAN?
Answer: It simplifies policy enforcement and traffic orchestration across a complex network. - What’s the primary security feature built into SD-WAN?
Answer: End-to-end encryption and segmentation. - What is the role of “multidomain” in SD-WAN?
Answer: It unifies data center, branch, and cloud connectivity into a single, secure architecture.
- What challenge does Cisco SD-WAN solve for modern businesses?
-
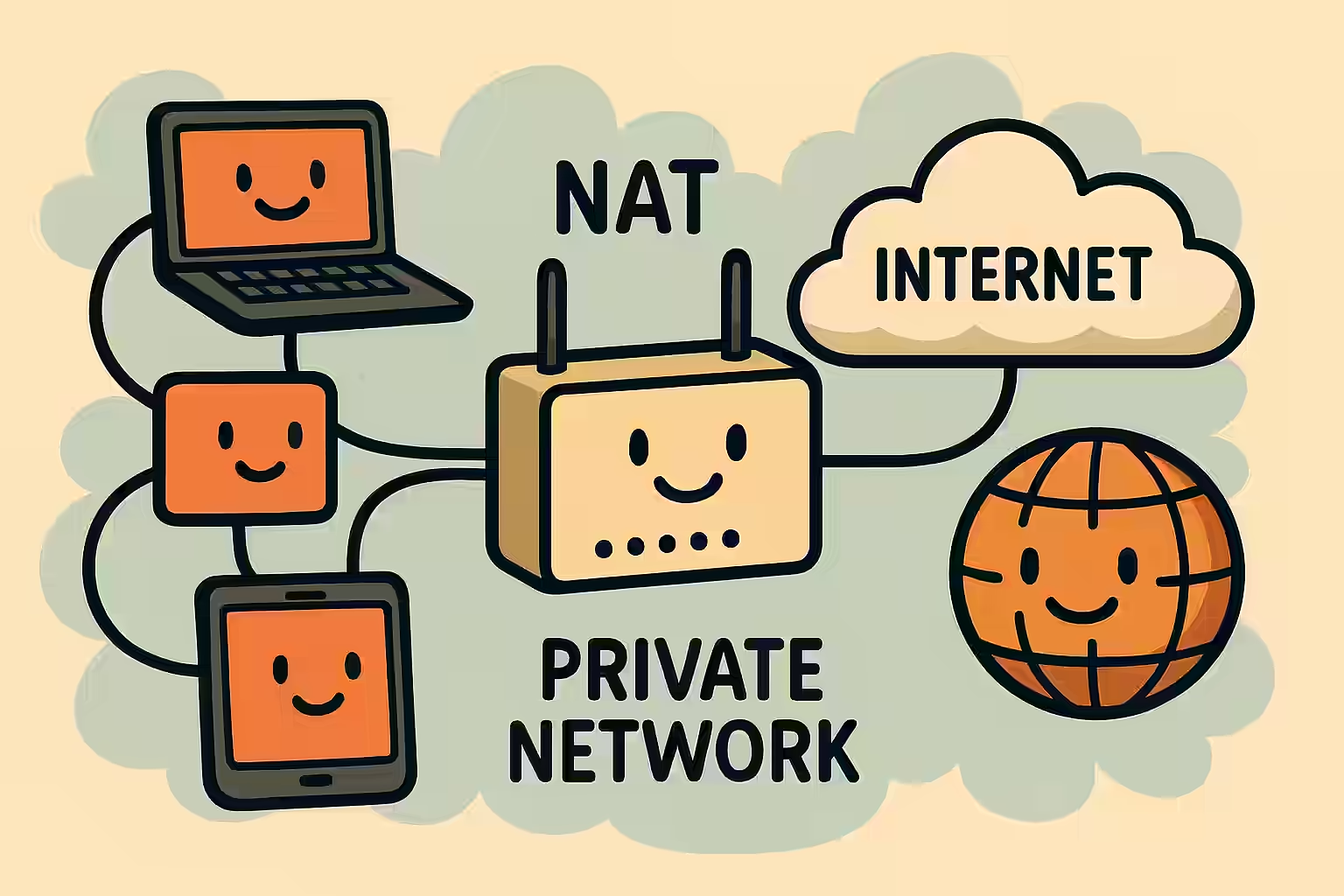
The Curious World of NAT: How One Router Can Rule Them All!
Imagine if your home’s Wi-Fi network had a gatekeeper — someone to decide which device gets to talk to the outside world and which messages come in. That’s the magic of Network Address Translation (NAT), a clever trick in every router’s bag that keeps your private network safe and efficient!
NAT is like the personal assistant you never knew you needed for your home or office network. It allows multiple devices to share a single public IP address, keeping your private network safe from the chaos of the internet. Let’s explore how it works and why it’s essential.
✅ What is NAT?
NAT stands for Network Address Translation. It’s a method used by routers to rewrite the source or destination IP addresses in packets as they cross from private networks to the internet (and vice versa).✅ Why NAT Matters:
- IP Conservation: NAT allows you to use a single public IP address for many internal devices.
- Security: External hosts can’t directly access internal IPs, adding a layer of protection.
- Simplicity: You don’t need a unique public IP for every device in your network!
✅ Types of NAT:
- Static NAT: Maps one internal IP to one external IP.
- Dynamic NAT: Chooses an available external IP from a pool for each session.
- PAT (Port Address Translation) or Overloading: Maps many internal IPs to one external IP, using different port numbers.
✅ Basic NAT Configuration Example:
Here’s a simple set of commands to configure PAT (the most common NAT type):Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255 Router(config)# ip nat inside source list 1 interface GigabitEthernet0/1 overload Router(config)# interface GigabitEthernet0/0 Router(config-if)# ip nat inside Router(config-if)# interface GigabitEthernet0/1 Router(config-if)# ip nat outsideThese commands tell the router to translate internal IPs to the public address on GigabitEthernet0/1 using PAT.
Why You Should Care:
Without NAT, we’d run out of IPv4 addresses in no time, and your home network would be exposed to all kinds of trouble. NAT keeps things neat, secure, and well-organized.
Quiz Time!
- What does NAT stand for?
- A) Network Address Table
- B) Network Address Translation
- C) Network Adapter Translation
- Answer: B
- Which NAT type uses one public IP for multiple devices?
- A) Static NAT
- B) PAT
- Answer: B
- True or False: NAT improves security.
- Answer: True
- What’s the main benefit of using NAT?
- Answer: Conserves IP addresses and adds security
- Fill in the blank: NAT rewrites ______ addresses in packets as they cross the router.
- Answer: IP
-
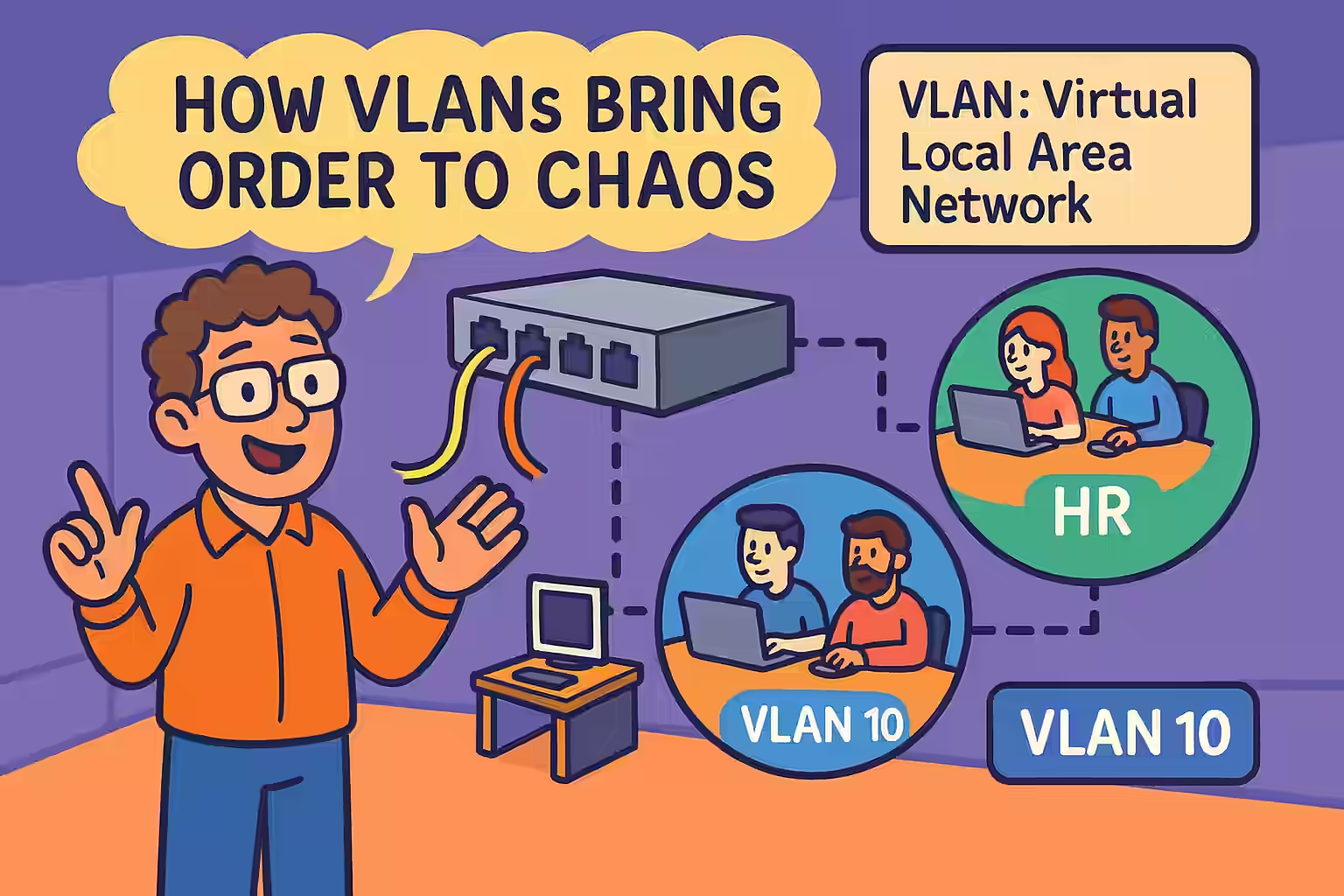
How VLANs Bring Order to Chaos: Your Guide to Virtual LANs
Ever felt like your home office was in chaos, with cables running amok and devices talking over each other? Well, imagine that, but on a much larger scale — that’s what unmanaged networks feel like! But fear not — VLANs are here to bring order to this chaos, one virtual boundary at a time!
Virtual LANs (VLANs) are like the bouncers at your favorite club: they make sure only the right folks get into the right rooms. In networking, VLANs logically segment a single physical network into multiple virtual networks, giving you better security, improved performance, and much easier management.
✅ What is a VLAN?
A VLAN is a virtual network within a switch or group of switches, logically dividing a broadcast domain — no new cables, just clever configurations!✅ Benefits of VLANs:
- Segmentation: Reduce broadcast domains, controlling who can talk to whom.
- Security: Isolate sensitive data and devices from the rest.
- Flexibility: Group users by department, not just by location.
✅ How VLANs Work:
- Tagged frames: VLANs use tags (like 802.1Q) to mark which VLAN each frame belongs to.
- Access ports vs. trunk ports: Access ports connect to end devices (one VLAN per port), while trunk ports connect switches (carrying multiple VLANs).
✅ Basic VLAN Configuration on a Cisco Switch:
Here’s a quick IOS command set to create and assign VLANs:Switch# configure terminal Switch(config)# vlan 10 Switch(config-vlan)# name HR Switch(config-vlan)# exit Switch(config)# interface FastEthernet 0/1 Switch(config-if)# switchport mode access Switch(config-if)# switchport access vlan 10And voilà! Port 0/1 is now part of VLAN 10, dedicated to the HR team!
Why VLANs Matter:
Without VLANs, every device would be in one big broadcast party, causing unnecessary traffic and security risks. VLANs help keep things tidy, efficient, and secure.
Quiz Time!
- What does VLAN stand for?
- A) Virtual Learning and Networking
- B) Virtual Local Area Network
- C) Visual LAN
- Answer: B
- What type of port carries multiple VLANs between switches?
- A) Access port
- B) Trunk port
- Answer: B
- True or False: VLANs require physical separation of devices.
- Answer: False
- What is the standard used for VLAN tagging?
- A) 802.3
- B) 802.11
- C) 802.1Q
- Answer: C
- Name one benefit of using VLANs.
- Answer: Improved security, reduced broadcast domains, or network flexibility.
-

Antennas and RF Signal Behavior: Navigating the Waves of Wireless Networking
We’ve talked about RF signals and the components that generate and measure them. Now, it’s time to focus on antennas—the unsung heroes of wireless—and understand how RF signals behave once they leave the antenna. This knowledge is essential for designing networks with optimal coverage and performance.
What is an Antenna?
An antenna is a device that converts electrical signals into electromagnetic waves and vice versa. It’s the interface between wired electronics and the wireless airwaves.
Antennas don’t create RF energy, but they radiate or receive it, acting as both launchpads and catchers of RF signals.
Types of Antennas
There’s no one-size-fits-all in antenna design. Different types serve different purposes:
Omnidirectional Antennas
- Radiate equally in all horizontal directions
- Great for covering open areas like warehouses or outdoor spaces
Directional Antennas
- Focus energy in a specific direction
- Ideal for long-distance point-to-point links or targeted coverage areas
Examples:
- Yagi: Focused beam, long range
- Patch/Panel: Flat and rectangular, used for indoor coverage
- Parabolic Dish: Extreme range, high gain
Sector Antennas
- Combine elements of both omni and directional
- Common in cellular towers to cover pie-shaped areas
Antenna Characteristics
Gain
- Measured in dBi or dBd, gain represents how well an antenna focuses energy.
- Higher gain = longer range but narrower beam
Beamwidth
- The width of the antenna’s main lobe of radiation, typically measured in degrees.
Polarization
- Refers to the orientation of the electric field (vertical, horizontal, or circular).
- Must match between transmitter and receiver for best performance.
RF Signal Behavior
Once a signal is radiated, it interacts with the environment in complex ways:
Reflection
- Bounces off surfaces like metal or glass
- Can cause multipath interference when signals arrive at slightly different times
Refraction
- Bends when it passes through materials of different densities (e.g., air to glass)
Diffraction
- Bends around obstacles, allowing coverage beyond line-of-sight
Scattering
- Occurs when signals hit small objects or rough surfaces, dispersing the wave
These behaviors affect signal strength, quality, and coverage area.
The Fresnel Zone
The Fresnel Zone is an elliptical area around the line-of-sight path between transmitter and receiver. Obstacles in this zone can interfere with the signal even if there’s no direct obstruction.
Clearing at least 60% of the Fresnel Zone ensures good signal quality.
Antenna Placement Best Practices
- Height matters: Higher placement reduces obstacles and improves line-of-sight
- Avoid metal objects: These can reflect or absorb RF energy
- Mind the Fresnel Zone: Ensure it’s clear to reduce interference
- Use appropriate polarization: Match antenna orientation
Real-World Tip
When planning coverage in a building with multiple floors, consider the antenna’s vertical radiation pattern. Most omnidirectional antennas focus energy horizontally—so floors above or below may get weaker signals.
Summary
Antennas are vital to getting your RF signals into and out of the air, and understanding how signals behave after transmission can make or break a wireless deployment. Knowing the difference between antenna types, how to interpret gain and beamwidth, and managing signal behaviors like reflection and diffraction helps you design more reliable and efficient networks.
In the next blog, we’ll dig into the IEEE 802.11 standards—the protocols that define how wireless LANs communicate. Get ready to learn the language of Wi-Fi!
-

Diving into RF Components, Measurements, and Mathematics: The Building Blocks of Wireless
In the last blog, we explored the mysterious world of Radio Frequency (RF) fundamentals. Now, it’s time to zoom in on the hardware and math that make wireless networking function. Understanding RF components, how we measure signals, and some key math concepts will give you a real edge in designing and troubleshooting wireless networks.
Key RF Components
Every wireless system includes components that either generate, transmit, receive, or manipulate RF signals. Here are the main players:
Transmitters
These are responsible for generating RF signals and sending them through the antenna. In WLANs, this could be your access point (AP).
Receivers
Receivers detect and process RF signals sent from a transmitter. Your wireless device’s network interface card (NIC) acts as a receiver.
Antennas
Antennas radiate or receive RF signals. They come in various types like:
- Omnidirectional: Broadcasts in all directions.
- Directional: Focuses the signal in one direction for greater range.
Amplifiers
These increase the power of RF signals. Power amplifiers boost signals before transmission, and low-noise amplifiers (LNAs) improve signal reception quality.
Cables and Connectors
They link components and can cause signal loss, known as insertion loss. High-quality, short cables are preferred to minimize degradation.
Filters
Filters block unwanted frequencies and allow desired ones to pass, enhancing signal clarity.
Measuring RF: The Decibel Scale
In wireless networking, we use decibels (dB) to measure signal levels and gains/losses. It’s a logarithmic scale, which means every 3 dB increase roughly doubles the power.
Common Units:
- dBm: Decibels relative to 1 milliwatt (used for signal strength).
- dBi: Antenna gain compared to an isotropic antenna.
- dBd: Antenna gain compared to a dipole antenna (2.14 dB less than dBi).
Signal Strength Guidelines:
- –30 dBm: Very strong
- –60 dBm: Good
- –90 dBm: Weak
RF Mathematics: Calculations That Matter
Wireless professionals rely on basic math to calculate coverage, link budgets, and signal strength. Here are some key formulas:
1. Free Space Path Loss (FSPL)
This calculates the loss of signal over distance in free space: FSPL (dB) = 20 log10(d) + 20 log10(f) – 147.55 Where:
- d = distance in meters
- f = frequency in MHz
2. Link Budget
Helps determine if the signal at the receiver will be strong enough: Link Budget = Transmit Power + Gains – Losses
3. EIRP (Effective Isotropic Radiated Power)
This measures total output power: EIRP = Transmit Power + Antenna Gain – Cable Loss
Real-World Application
Imagine deploying Wi-Fi in a large office. You’ll:
- Choose antennas based on coverage needs
- Calculate path loss to ensure signal reaches all areas
- Use link budget to decide if amplifiers are needed
Understanding these RF components and calculations is like having x-ray vision into how your wireless network is functioning.
Summary
RF components and their related measurements form the spine of wireless network engineering. Transmitters, receivers, antennas, and amplifiers all play their part, while decibel measurements and simple math allow us to predict and optimize performance. In the next blog, we’ll dive into the fascinating world of antennas and RF signal behavior. Don’t miss it!
-

Understanding Radio Frequency (RF) Fundamentals: The Invisible Engine of Wireless Communication
If wireless standards are the laws of the land, then Radio Frequency (RF) is the terrain itself. Understanding RF is absolutely crucial to mastering wireless networking, and in this blog, we’ll demystify the invisible forces that power every Wi-Fi connection, Bluetooth signal, and cellular conversation.
What is RF?
Radio Frequency refers to electromagnetic wave frequencies that range from 3 kHz to 300 GHz. These waves travel through the air and carry information across distances without the need for physical wires. Wireless networks use specific RF bands to transmit and receive data.
The Electromagnetic Spectrum
The electromagnetic spectrum encompasses all types of electromagnetic radiation, from gamma rays to radio waves. RF occupies a small but vital slice of this spectrum:
- Very Low Frequency (VLF): 3 to 30 kHz
- Low Frequency (LF): 30 to 300 kHz
- Medium Frequency (MF): 300 kHz to 3 MHz
- High Frequency (HF): 3 to 30 MHz
- Very High Frequency (VHF): 30 to 300 MHz
- Ultra High Frequency (UHF): 300 MHz to 3 GHz
- Super High Frequency (SHF): 3 to 30 GHz
- Extremely High Frequency (EHF): 30 to 300 GHz
Wi-Fi networks typically operate in the UHF and SHF ranges, particularly 2.4 GHz and 5 GHz, and now even 6 GHz with Wi-Fi 6E.
Frequency, Wavelength, and Amplitude
To understand how RF works, we need to get comfortable with three core concepts:
Frequency
This is the number of times a wave cycles in one second, measured in Hertz (Hz). Higher frequencies mean more data can be carried, but the range is shorter.
Wavelength
This is the physical length of one complete wave cycle. There is an inverse relationship between wavelength and frequency: higher frequency = shorter wavelength.
Amplitude
Amplitude is the height of the wave. It represents the signal strength or power level. More amplitude means a stronger signal.
Modulation: Making Waves Work for Us
Modulation is how we embed information into RF signals. Three common types of modulation are:
- Amplitude Modulation (AM)
- Frequency Modulation (FM)
- Phase Modulation (PM)
In wireless networking, more complex modulation schemes like Quadrature Amplitude Modulation (QAM) are used to squeeze more data into the same bandwidth.
RF Behavior: Predictable but Tricky
RF doesn’t just fly straight and true. It can behave in ways that complicate network design:
- Reflection: Bouncing off surfaces like walls or metal
- Refraction: Bending as it passes through different materials
- Diffraction: Spreading out when it hits an obstacle
- Scattering: Splintering into many weaker waves due to small objects
Understanding these behaviors helps in designing robust, reliable networks.
Attenuation and Interference
Attenuation
RF signals lose strength over distance or when passing through materials. This loss is called attenuation, and it’s a major factor in determining wireless coverage.
Interference
Other electronic devices, neighboring Wi-Fi networks, and even microwaves can interfere with RF signals, leading to degraded performance.
Decibels and Signal Measurement
Wireless professionals use decibels (dB) to measure signal strength and loss:
- dBm: Signal strength referenced to 1 milliwatt
- dBi: Antenna gain compared to an isotropic antenna
- dBd: Antenna gain compared to a dipole antenna
For example:
- –60 dBm = weak signal
- –30 dBm = strong signal
The Importance of RF in CWNA
As a CWNA candidate, RF knowledge is your secret weapon. It empowers you to:
- Design smarter wireless networks
- Troubleshoot signal issues
- Optimize coverage and performance
Mastering RF is like learning the language of wireless. Once you understand how these invisible waves work, you’ll see the entire network in a new light.
Summary
RF may be invisible, but its effects are everywhere. By understanding frequency, wavelength, modulation, and signal behavior, you lay the foundation for becoming a wireless networking expert. In our next blog, we’ll explore the physical components that transmit and receive these signals: antennas and RF measurements. Stay tuned!
